1-click AWS Deployment 1-click Azure Deployment
Overview
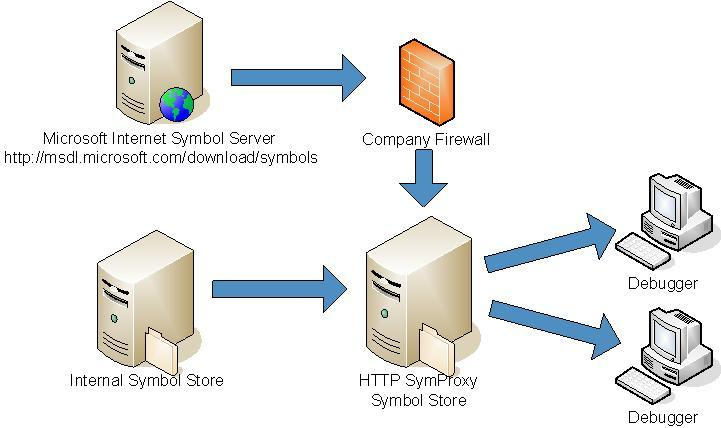
You can configure your HTTP-based symbol store to act as a proxy between client computers and other symbol stores. The implementation is through an Internet Server Application Programming Interface (ISAPI) filter called SymProxy (Symproxy.dll). The SymProxy server can be used as a gateway computer to the Internet or other sources within your company network. The following diagram shows an example SymProxy configuration.
Utility:
SymProxy is useful in many situations. For example:
- You are debugging many systems within a lab environment in which the computers are not attached to the company network, but the symbols are stored in the network and must be accessed using Integrated Windows Authentication (IWA).
- Your corporate computing environment includes a firewall that prevents access to the Internet from computers that are debugging and you must obtain symbols from an internet Web site.
- You want to present a single symbol path for all users in your company so that they need not know or care about where symbols are located, and you can add new symbol stores without user intervention.
- You have a remote site that is physically far from the rest of your company resources, and network access is slow. This system can be used to acquire symbols and cache them to the remote site.
- To install SymProxy, you must manually copy the files to the correct location, configure the registry, choose network security credentials, and configure Internet Information Services (IIS).
Multiple Symbol Server Performance Considerations
Each Virtual Directory can be associated with multiple (upstream) symbol stores. Each symbol store is queried independently. For performance, local SMB servers should be processed before internet HTTP servers. Unlike a debugger symbol path, multiple HTTP symbol stores can be specified in a SymProxy symbol path. A maximum of 10 entries are supported per Virtual Directory.
SymProxy Symbol Path
SymProxy splits the (registry defined) symbol path value up in to the individual entries and uses each entry to generate a SRV* based symbol path to retrieve the file. It uses the Virtual Directory’s folder as the downstream store in each of the queries – in effect, merging the upstream stores in to a single downstream symbol store.
The (generated) symbol path used by SymProxy is equivalent to this:
SRV*<Virtual Directory Folder>*<SymbolPath Entry #N>
In this example, a UNC path and two HTTP paths are associated with a Virtual Directory to merge the symbols from a corporate symbol server, Microsoft and a 3rd party (Contoso). The SymProxy SymbolPath would be set like this:
\\MainOffice\Symbols;https://msdl.microsoft.com/download/symbols;
https://symbols.contoso.com/symbols
The Main Office Symbol file share is queried first using a (generated) symbol path of:
SRV*D:\SymStore\Symbols*\\MainOffice\Symbols
If the symbol file is not found, the Microsoft Symbol Store is queried using a (generated) symbol path of:
SRV*D:\SymStore\Symbols*https://msdl.microsoft.com/download/symbols
If the file is still not found, the Contoso Symbol Store (https://symbols.contoso.com/symbols) is queried using a (generated) symbol path of:
SRV*D:\SymStore\Symbols*https://symbols.contoso.com/symbolsInstalling SymProxy:
Summary of installation tasks
The following summarizes the tasks to install and configure SymProxy.
- The SymProxy files need to be copied to the %WINDIR%\system32\inetsrv folder for IIS. This task is discussed below.
- The registry needs to be configured for SymProxy. For more information see Configuring the Registry.
- The manifest needs to be registered as Performance Counters and ETW events, and the Event Log needs to be configured.
- IIS needs to be configured. For more information, see Choosing Network Security Credentials and Configuring IIS for SymProxy.
These steps can be automated using the Install.cmd file. For more information, see SymProxy Automated Installation.
Copy the SymProxy files to IIS
The SymProxy files are included in the Debuggers directory of the Windows Driver Kit. For example this is the location of the 64 bit files for Windows 10 kit. C:\Program Files (x86)\Windows Kits\10\Debuggers\x64\symproxy.
To install SymProxy on the server, copy symproxy.dll, symsrv.dll and symproxy.man to %WINDIR%\system32\inetsrv.
In order to prevent problems that could occur in accessing the Microsoft Symbol Store, create a blank file called %WINDIR%\system32\inetsrv\symsrv.yes. The contents of this file are not important. When symsrv.yes file is present, it automatically accepts the EULA for the Microsoft Public Symbol Store.
Note that the certificates that are normally installed with IIS and Windows server such as the “Baltimore CyberTrust Root” are used for HTTPS/TLS communication to the upstream provider, and they need to be in the Trusted Root store on the machine where SymProxy is running.
SymProxy Automated Installation:
These steps along with the Install.cmd script below can help automate the installation of SymProxy to a default IIS installation. You will likely need to adapt these steps to the specific needs of your environment.
- Create D:\SymStore\Symbols folder.
- Grant Read to Everyone
- Grant Read\Write to the SymProxy App Pool user account (Domain\User)
- Share D:\SymStore\Symbols as Symbols.
- Grant Read to Everyone (or be more specific)
- (Optionally) Create an empty file called index2.txt in D:\SymStore\Symbols.
- (Optionally) Create an empty file called %WINDIR%\system32\inetsrv\symsrv.yes. This accepts the EULA for the Microsoft Public Symbol Store.
- Determine the parameters for Install.cmd and run it.
- Configure the clients symbol path using the server name that you created.
SRV*\\MachineName\Symbols*https://MachineName/Symbols
The Install.cmd script requires 3 parameters:
- Virtual Directory path (e.g. D:\SymStore\Symbols )
- Username (for the Application Pool)
- Password (for the Application Pool)
To clear the MIME Type inheritance, an XML file is needed to drive the associated AppCmd.exe command. Place the staticContentClear.xml file shown below in the same folder as the Install.cmd script to achieve this result.
Example Install.Cmd parameter usage:
Install.cmd D:\SymStore\Symbols CONTOSO\SymProxyService Pa$$word
Install.cmd
@echo off
SET VirDirectory=%1
SET UserName=%2
SET Password=%3
::
:: SymProxy dll installation.
::
copy symproxy.dll %windir%\system32\inetsrv
copy symproxy.man %windir%\system32\inetsrv
copy symsrv.dll %windir%\system32\inetsrv
lodctr.exe /m:%windir%\system32\inetsrv\symproxy.man
wevtutil.exe install-manifest %windir%\System32\inetsrv\symproxy.man
regedit.exe /s symproxy.reg
::
:: Web server Configuraiton
::
IF not exist %VirDirectory% mkdir %VirDirectory%
rem Make the 'Default Web Site'
%windir%\system32\inetsrv\appcmd.exe add site -site.name:"Default Web Site" -bindings:"http/*:80:" -physicalPath:C:\inetpub\wwwroot
rem Enabled Directory Browsing on the 'Default Web Site'
%windir%\system32\inetsrv\appcmd.exe set config "Default Web Site" -section:system.webServer/directoryBrowse /enabled:"True"
rem Make the 'SymProxy App Pool'
%windir%\system32\inetsrv\appcmd.exe add apppool -apppool.name:SymProxyAppPool -managedRuntimeVersion:
%windir%\system32\inetsrv\appcmd.exe set apppool -apppool.name:SymProxyAppPool -processModel.identityType:SpecificUser -processModel.userName:%UserName% -processModel.password:%Password%
rem Make the 'Symbols' Virtual Directory and assign the 'SymProxy App Pool'
%windir%\system32\inetsrv\appcmd.exe add app -site.name:"Default Web Site" -path:/Symbols -physicalpath:%VirDirectory%
%windir%\system32\inetsrv\appcmd.exe set app -app.name:"Default Web Site/Symbols" -applicationPool:SymProxyAppPool
rem Disable 'web.config' for folders under virtual directories in the 'Default Web Site'
%windir%\system32\inetsrv\appcmd.exe set config -section:system.applicationHost/sites "/[name='Default Web Site'].virtualDirectoryDefaults.allowSubDirConfig:false
rem Add the 'SymProxy ISAPI Filter'
%windir%\system32\inetsrv\appcmd.exe set config -section:system.webServer/isapiFilters /+"[name='SymProxy',path='%windir%\system32\inetsrv\SymProxy.dll',enabled='True']
rem Clear the MIME Types on the 'Default Web Site'
%windir%\system32\inetsrv\appcmd.exe set config -in "Default Web Site" < staticContentClear.xml
rem Add * to the MIME Types of the 'Default Web Site'
%windir%\system32\inetsrv\appcmd.exe set config "Default Web Site" -section:staticContent /+"[fileExtension='.*',mimeType='application/octet-stream']"
staticContentClear.xml
<?xml version="1.0" encoding="UTF-8"?>
<appcmd>
<CONFIG CONFIG.SECTION="system.webServer/staticContent" path="MACHINE/WEBROOT/APPHOST">
<system.webServer-staticContent>
<clear />
</system.webServer-staticContent>
</CONFIG>
</appcmd>
Testing the SymProxy Installation
The system should now be ready to acquire and serve files. To test it, start by restarting the IISAdmin service by running iisreset.exe. This will reload the ISAPI filter with the current IIS and SymProxy configuration.
Configure a debugger to use this symbol path:
srv*\\MachineName\Symbols*https://MachineName/Symbols
If MissTimeout is enabled (it is set to 300 seconds by default), running the .reload /f command twice should result in much faster execution the second time.
To view the location of the PDBs being referenced, use the lm (list modules) command. The path to the PDBs should all begin with \\MachineName\Symbols.
If directory browsing is enabled on the web site, browse to https://MachineName/Symbols to see the files that are cached.
Open the Performance Monitor and view the Symbol Proxy counters.
Open the Event Viewer and view the Microsoft\Windows\SymProxy events.
Features
Major Features of Symproxy :
SymProxy is useful in many situations. For example:
- You are debugging many systems within a lab environment in which the computers are not attached to the company network, but the symbols are stored in the network and must be accessed using Integrated Windows Authentication (IWA).
- Your corporate computing environment includes a firewall that prevents access to the Internet from computers that are debugging and you must obtain symbols from an internet Web site.
- You want to present a single symbol path for all users in your company so that they need not know or care about where symbols are located, and you can add new symbol stores without user intervention.
- You have a remote site that is physically far from the rest of your company resources, and network access is slow. This system can be used to acquire symbols and cache them to the remote site.
Videos
Microsoft Symbol Proxy SymProxy


