1-click AWS Deployment 1-click Azure Deployment
Overview
Redis, developed in 2009, is a flexible, open-source (BSD licensed), in-memory data structure store, used as database, cache, and message broker. Following in the footsteps of other NoSQL databases, such as Cassandra, CouchDB, and MongoDB, Redis allows the user to store vast amounts of data without the limits of a relational database.
It supports various data structures such as strings, hashes, sets, lists, sorted sets, bitmaps, hyperloglogs and geospatial indexes with radius queries.Redis has built-in replication, Lua scripting, LRU eviction, transactions and different levels of on-disk persistence, and provides high availability via Redis Sentinel and automatic partitioning with Redis Cluster.
Redis can be compiled and used on Linux, OSX, OpenBSD, NetBSD, FreeBSD. It supports big endian and little endian architectures, and both 32 bit and 64 bit systems.Redis is maintained and developed by Salvatore Sanfilippo. In the past, Pieter Noordhuis and Matt Stancliff provided a very significant amount of code and ideas to both the Redis core and client libraries.
What does the name Redis mean?
Redis stands for REmote DIctionary Server.
What is Redis used for?
Redis is an advanced key-value store that can function as a NoSQL database or as a memory-cache store to improve performance when serving data that is stored in system memory.
How to interact with Redis?
Once installed in a server, run the Redis CLI (Command Line Interface) to issue commands to Redis. While working on the CLI tool, your command-line prompt will change to: redis>
What happens if Redis runs out of memory?
Redis will either be killed by the Linux kernel OOM killer, crash with an error or will start to slow down. With modern operating systems malloc() returning NULL is not common, usually the server will start swapping, and Redis performance will degrade, so you’ll probably notice there is something wrong.The INFO command will report the amount of memory Redis is using so you can write scripts that monitor your Redis servers checking for critical conditions.Redis has built-in protections allowing the user to set a max limit to memory usage, using the maxmemory option in the config file to put a limit to the memory Redis can use. If this limit is reached Redis will start to reply with an error to write commands, or you can configure it to evict keys when the max memory limit is reached in the case you are using Redis for caching.You can easily build complex systems on top of Redis, here is a sample list :
- User defined indexing schemes
- Message queues with real time new element notification
- Directed and undirected graph stores for following or friending systems
- Real-time publish/subscribe notification systems
- Real-time analytics backends
- Bloom filter servers
- Task queues and job systems
- High score leaderboards
- User ranking systems
- Hierarchical/tree structured storage systems
- Individual personalized news or data feeds for your users
Redis’s simplicity, exceptionally speedy performance, as well as atomic manipulation of the data structures, offers itself for solving problems that are difficult or perform weakly when implemented along with the traditional relational databases. Some popular applications of Redis due to its versatile nature are as follows:
1. Queues – The projects such as Rescue makes use of Redis for the backend for queueing background jobs.
2. Publish and Subscribe – From the time of launch of version 2.0, Redis offers the capability to distribute the data by utilizing the Publish/Subscribe paradigm. Some of the organizations have shifted to Redis and gone away from the other message queuing systems (such as RabbitMQ, zerm, etc.) only because of Redis’s reliable performance and its simplicity.
3. Caching – Because of its high performance, a number of developers have turned to Redis at the time when the read and write operations volume exceeds the capabilities of the traditional databases. With its ability to persist the data to disk, Redis is considered to be a superior alternative as compared to the traditional solution for caching.
4. Counters – The atomic commands such as HINCRBY, gives access for simple and thread-safe implementation of the various counters. Forming a counter is as easy as determining the name for a key and then issuing a HINCRBY command. It is of no use to even read the data before incrementing it, and there are even no database schemes to be updated. As these are atomic operations that take place, the counters will assist in maintaining consistency when they are accessed from multiple application servers.
Famous organizations using REDIS
Redis has garnered and catered to the needs of its multiple users. Some important qualities that set apart Redis from the other key-value databases are that Redis has the ability to store as well as manipulate the high-level data types. Such data types are the fundamental data structures such as maps, sets, lists, as well as assorted sets. These are some of the data types which most of the developers are familiar with. Due to such ease of usage, Redis has found its place in the operating systems of popular organizations. Below mentioned are the details of how Redis is used in a particular organization.
1. GitHub –GitHub is said to be a web-based hosting service for the purpose of software development projects which use the Git revision control system. It offers paid plans for private repositories, as well as free accounts for the open-source projects. GitHub is presently considered to be the most famous code repository site for open source projects. GitHub was an early adopter of the Redis project. It has developed and open-sourced a library called Rescue, in order to facilitate the execution of the background jobs which have been placed in a queue. The GitHub developers took advantage of the fact that Redis was able to solve many of their difficult queueing issues. Thus the developers could remain focused on the difficult worker scheduling tasks.
2. Pinterest – Pinterest is a popular image website that has images based on different themes. Users are allowed to view, share as well as download high-quality images. Pinterest stores the user follower graphs within a Redis cluster where the data is shared with hundreds of different instances. Pinterest had started to use Redis after it found that their earlier solution of MySQL and Memcached had been reaching its limits.
3. Twitter – Twitter is a popular social networking site that allows users to share their views and opinions. Twitter has deployed a huge Redis cluster in order to store the timelines of all the users of the website. By utilizing the list of the data structure, Twitter is able to store the 800 most recent incoming tweets of a given user.
Redis vs Other Key-Value Stores
Key-value store is a special type of database storage system where data is stored in form of key and value pairs.
Redis is different compared to other key-value stores because of the following:
- Redis is a different evolution path in the key-value databases where values can contain more complex data types, with atomic operations defined on those data types.
- Redis data types are closely related to fundamental data structures and are exposed to the programmer as such, without additional abstraction layers.
- Redis is an in-memory but persistent on disk database, so it represents a different trade off where very high write and read speed is achieved with the limitation of data sets that can’t be larger than memory.
- Another advantage of in memory databases is that the memory representation of complex data structures is much simpler to manipulate compared to the same data structure on disk, so Redis can do a lot, with little internal complexity.
- At the same time the two on-disk storage formats (RDB and AOF) don’t need to be suitable for random access, so they are compact and always generated in an append-only fashion.
Redis Installation
Installation
To install the Redis on Ubuntu, go to terminal and type the following commands:
Start Redis
Redis Data Types
Redis is not a plain key-value store, actually, it is a data structures server, supporting a different kind of values. In traditional key-value stores, you associated string keys to string values, in Redis the value is not limited to a simple string, but can also hold more complex data structures. The following is the list of all the data structures supported by Redis:
- Binary-safe strings.
- Lists
- Sets
- Sorted sets
- Hashes
- Bit arrays (or simply bitmaps)
- HyperLogLogs:
Redis keys:
Redis keys are binary safe (meaning they have a known length not determined by any special terminating characters), so you can use any binary sequence as a key, from a string like “foo” to the content of a JPEG file. The empty string is also a valid key. Here are some rules about keys:
- The maximum allowed key size is 512 MB.
- Very long keys are not a good idea.
- Very short keys are often not a good idea. While short keys will obviously consume a bit less memory, your job is to find the right balance.
- Try to stick with a schema. For instance “object-type:id” is a good idea, as in “user:1000”. Dots or dashes are often used for multi-word fields, as in “comment:1234:reply.to” or “comment:1234:reply-to”.
Redis Strings:
Strings are Redis’ most basic data type. It is the only data type in Memcached, so it is also very natural for newcomers to use it in Redis. Since Redis keys are strings, when we use the string type as a value too, we are mapping a string to another string. The string data type is useful for a number of use cases, like caching HTML fragments or pages. Here are some common commands associated with strings:
- SET: sets a value to a key
- GET: gets a value from a key
- DEL: deletes a key and its value
- INCR: atomically increments a key
- INCRBY: increments a key by a designated values
- EXPIRE: the length of time that a key should exist (denoted in seconds)
Strings can be used to store objects, arranged by key.
127.0.0.1:6379> SET newkey "the redis string" OK 127.0.0.1:6379> GET newkey "the redis string"
Redis Lists:
Lists in Redis are a collection of ordered values. This is in contrast to Sets which are unordered. Redis lists are implemented via Linked Lists. This means that even if you have millions of elements inside a list, the operation of adding a new element in the head or in the tail of the list is performed in constant time. Here are some common commands associated with lists:
- LPUSH: Add a value to the begriming of a list
- RPUSH: Add a value to the end of a list
- LPOP: Get and remove the first element in a list
- RPOP: Get and remove the last element in a list
- LREM: Remove elements from a list
- LRANGE: Get a range of elements from a list
- LTRIM: Modifies a list so leave only a specified range
Example:
redis 127.0.0.1:6379> lpush w3resourcelist redis (integer) 1 redis 127.0.0.1:6379> lpush w3resourcelist mongodb (integer) 2 redis 127.0.0.1:6379> lpush w3resourcelist rabitmq (integer) 3 redis 127.0.0.1:6379> lrange w3resourcelist 0 10 1) "rabitmq" 2) "mongodb" 3) "redis"
Redis Sets:
Redis Sets are unordered collections of strings. If you want to combine strings, you can do that with REDIS sets. Here are some common commands associated with sets:
- SADD: Add one or members to a set
- SMEMBERS: Get all set members
- SINTER: Find the intersection of multiple sets
- SISMEMBER: check if a value is in a set
- SRANDMEMBER: Get a random set member
Sets can be helpful in various situations. In sets each member of a set is unique, adding members to a set does not require a “check then add” operation. Instead the set will check whether the item is a duplicate whenever an SADD command is performed.
Example:
redis 127.0.0.1:6379> sadd w3resourcelist redis (integer) 1 redis 127.0.0.1:6379> sadd w3resourcelist mongodb (integer) 1 redis 127.0.0.1:6379> sadd w3resourcelist rabitmq (integer) 1 redis 127.0.0.1:6379> sadd w3resourcelist rabitmq (integer) 0 redis 127.0.0.1:6379> smembers w3resourcelist 1) "rabitmq" 2) "mongodb" 3) "redis"
Redis Sorted sets:
Sorted sets are a data type which is similar to a mix between a Set and a Hash. Like sets, sorted sets are composed of unique, non-repeating string elements, so in some sense, a sorted set is a set as well.
However, while elements inside sets are not ordered, every element in a sorted set is associated with a floating point value, called the score (this is why the type is also similar to a hash, since every element is mapped to a value). Here are some common commands associated with sorted sets :
- ZADD: Adds members to a sorted set
- ZRANGE: Displays the members of a sorted set arranged by index (with the default low to high)
- ZREVRANGE: Displays the members of a sorted set arranged by index (from high to low)
- ZREM: Removes members from a sorted set
Example:
redis 127.0.0.1:6379> zadd w3resourcelist 0 redis (integer) 1 redis 127.0.0.1:6379> zadd w3resourcelist 0 mongodb (integer) 1 redis 127.0.0.1:6379> zadd w3resourcelist 0 rabitmq (integer) 1 redis 127.0.0.1:6379> zadd w3resourcelist 0 rabitmq (integer) 0 redis 127.0.0.1:6379> ZRANGEBYSCORE w3resourcelist 0 1000 1) "redis" 2) "mongodb" 3) "rabitmq"
Redis Hashes:
Hashes in Redis are useful to represent objects with many fields. They are set up to store a vast amount of fields in a small amount of space. Here are some common commands associated with hashes:
- HMSET: Sets up multiple hash values
- HSET: Sets the hash field with a string value
- HGET: Retrieves the value of a hash field
- HMGET: Retrieves all of the values for given hash fields
- HGETALL: Retrieves all of the values for in a hash
Example:
In the following example hash, data type is used to store user’s object which contains basic information of a user.
redis 127.0.0.1:6379> HMSET user:1 username w3resource password 123456 points 200 OK redis 127.0.0.1:6379> HGETALL user:1 1) "username" 2) "w3resource" 3) "password" 4) "123456" 5) "points" 6) "200"
Redis Bit arrays (or simply bitmaps):
It is possible, using special commands, to handle String values like an array of bits: you can set and clear individual bits, count all the bits set to 1, find the first set or unset bit, and so forth.
HyperLogLogs:
This is a probabilistic data structure which is used in order to estimate the cardinality of a set.
Redis – Commands
Redis commands are used to perform some operations on Redis server.To run commands on Redis server, you need a Redis client. Redis client is available in Redis package, which we have installed earlier.
Syntax
Following is the basic syntax of Redis client.
$redis-cli
Example
Following example explains how we can start Redis client.
To start Redis client, open the terminal and type the command redis-cli. This will connect to your local server and now you can run any command.
$redis-cli redis 127.0.0.1:6379> redis 127.0.0.1:6379> PING PONG
In the above example, we connect to Redis server running on the local machine and execute a command PING, that checks whether the server is running or not.
Run Commands on the Remote Server
To run commands on Redis remote server, you need to connect to the server by the same client redis-cli
Syntax
$ redis-cli -h host -p port -a password
Example
Following example shows how to connect to Redis remote server, running on host 127.0.0.1, port 6379 and has password mypass.
$redis-cli -h 127.0.0.1 -p 6379 -a "mypass" redis 127.0.0.1:6379> redis 127.0.0.1:6379> PING PONG
Redis – Keys
Redis keys commands are used for managing keys in Redis. Following is the syntax for using redis keys commands.
Syntax
redis 127.0.0.1:6379> COMMAND KEY_NAME
Example
redis 127.0.0.1:6379> SET tutorialspoint redis OK redis 127.0.0.1:6379> DEL tutorialspoint (integer) 1
In the above example, DEL is the command, while tutorialspoint is the key. If the key is deleted, then the output of the command will be (integer) 1, otherwise it will be (integer) 0.
Redis Keys Commands
Following table lists some basic commands related to keys.
| Sr.No | Command & Description |
|---|---|
| 1 | DEL keyThis command deletes the key, if it exists. |
| 2 | DUMP keyThis command returns a serialized version of the value stored at the specified key. |
| 3 | EXISTS keyThis command checks whether the key exists or not. |
| 4 | EXPIRE key secondsSets the expiry of the key after the specified time. |
| 5 | EXPIREAT key timestampSets the expiry of the key after the specified time. Here time is in Unix timestamp format. |
| 6 | PEXPIRE key millisecondsSet the expiry of key in milliseconds. |
| 7 | PEXPIREAT key milliseconds-timestampSets the expiry of the key in Unix timestamp specified as milliseconds. |
| 8 | KEYS patternFinds all keys matching the specified pattern. |
| 9 | MOVE key dbMoves a key to another database. |
| 10 | PERSIST keyRemoves the expiration from the key. |
| 11 | PTTL keyGets the remaining time in keys expiry in milliseconds. |
| 12 | TTL keyGets the remaining time in keys expiry. |
| 13 | RANDOMKEYReturns a random key from Redis. |
| 14 | RENAME key newkeyChanges the key name. |
| 15 | RENAMENX key newkeyRenames the key, if a new key doesn’t exist. |
| 16 | TYPE keyReturns the data type of the value stored in the key. |
Redis Backup & Restore
SAVE command is used to create a backup of a current Redis database. This command will create a dump.rdb file in your Redis directory by performing synchronous save.
Syntax
- SAVE
Return Value The SAVE command returns OK after successful execution.
Redis Backup Example
Use the SAVE command to create a backup of the current database.
SAVE
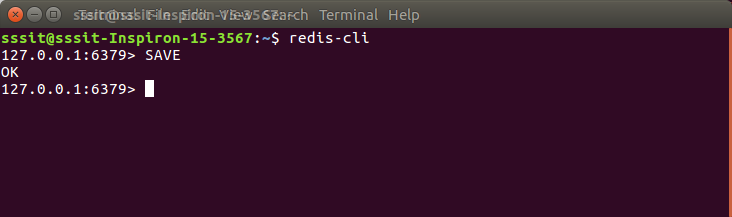
It will create a dump.rdb file in your Redis directory.You can see that the dump.rdb file is created.
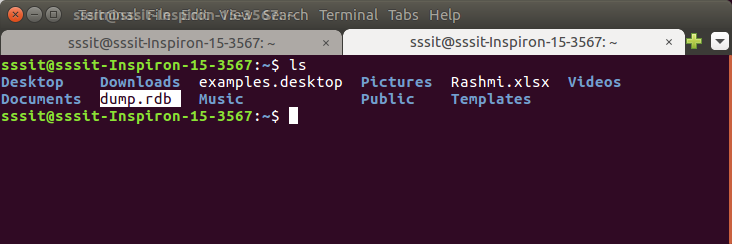
Restore Redis Data
You have to move Redis backup file (dump.rdb) into your Redis directory and start the server to restore Redis data.Use CONFIG command of Redis as shown below.
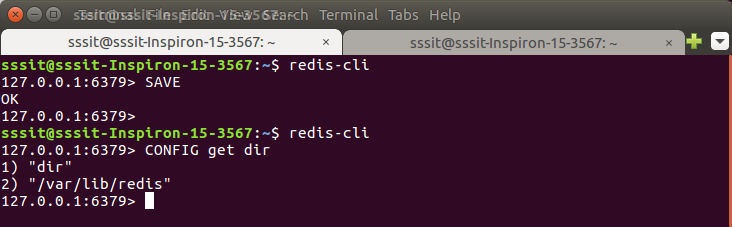
The Redis server is installed in the following directory.
“/var/lib/redis”
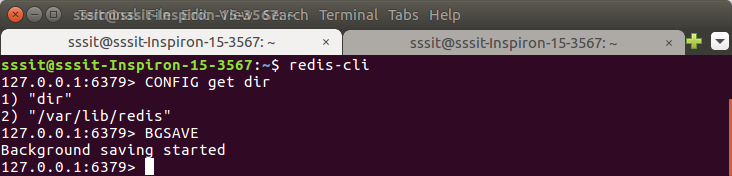
BGSAVE Command
There is an alternate command named BGSAVE which is used to create Redis backup.
This command will start the backup process and run this in the background.
Syntax
- BGSAVE
Example
Redis Security
Security is very necessary for a database to keep the data safe and secure. It provides an authentication so if a client want to make a connection needs to authenticate before executing a command.
You need to set a password in the config file to secure a Redis databse.
Example
Let’s see how to secure your Redis instance.Use the “config get command”
- config get requirepass
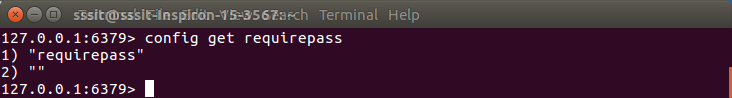
You can see that the above property is blank means we don’t have any password for this instance. You can change this property and set a password for this instance by executing the following command.
- config set requirepass “javatpoint123”
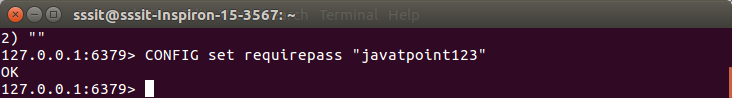
- CONFIG get requirepass
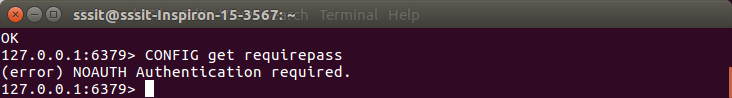
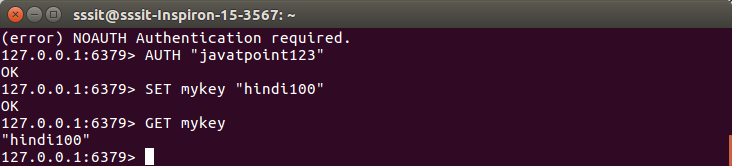
When you set this password then if a client runs the command without authentication, he will get an error “NOAUTH Authentication required.”. Hence, the client needs to use AUTH command to authenticate himself.
Usage of AUTH Command
- 127.0.0.1:6379> AUTH “javatpoint123”
- OK
- 127.0.0.1:6379> SET mykey “hindi100”
- OK
- 127.0.0.1:6379> GET mykey
- “hindi100”
- 127.0.0.1:6379>
Redis Client Connection
Redis can accept different type of clients’ connections on the configured listening TCP port and on the Unix socket, if enabled.
When a new client connection is accepted, it performs the following operations:
- The client socket is put in non-blocking state since Redis uses multiplexing and non-blocking I/O.
- The TCP_NODELAY option is set in order to ensure that we don’t have delays in our connection.
- A readable file event is created so that Redis is able to collect the client queries as soon as new data is available to be read on the socket.
Maximum number of Clients
In Redis config (redis.conf), there is a property called maxclients, which specifies that how many number of clients can be connected to Redis.Following is the basic syntax of command.
- Config get maxclients
- “maxclients”
- “4064”
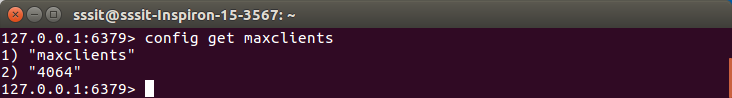
The maximum number of clients depends upon the maximum number of file descriptors limit of OS. Its default value is 10000, although you can change this property.
Example
Let’s take an example to set the maximum number of clients to 100000, while starting the server.
- redis-server –maxclients 100000
Client Commands
| Index | Command | Description |
|---|---|---|
| 1 | CLIENT LIST | Returns the list of clients connected to Redis server |
| 2 | CLIENT SETNAME | Assigns a name to the current connection |
| 3 | CLIENT GETNAME | Returns the name of the current connection as set by CLIENT SETNAME |
| 4 | CLIENT PAUSE | This is a connections control command able to suspend all the Redis clients for the specified amount of time (in milliseconds) |
| 5 | CLIENT KILL | This command closes a given client connection. |
Redis – Partitioning
Partitioning is the process of splitting your data into multiple Redis instances, so that every instance will only contain a subset of your keys.
Benefits of Partitioning
- It allows for much larger databases, using the sum of the memory of many computers. Without partitioning you are limited to the amount of memory that a single computer can support.
- It allows to scale the computational power to multiple cores and multiple computers, and the network bandwidth to multiple computers and network adapters.
Disadvantages of Partitioning
- Operations involving multiple keys are usually not supported. For instance, you can’t perform the intersection between two sets if they are stored in the keys that are mapped to different Redis instances.
- Redis transactions involving multiple keys cannot be used.
- The partitioning granuliary is the key, so it is not possible to shard a dataset with a single huge key like a very big sorted set.
- When partitioning is used, data handling is more complex. For instance, you have to handle multiple RDB/AOF files, and to get a backup of your data you need to aggregate the persistence files from multiple instances and hosts.
- Adding and removing the capacity can be complex. For instance, Redis Cluster supports mostly transparent rebalancing of data with the ability to add and remove nodes at runtime. However, other systems like client-side partitioning and proxies don’t support this feature. A technique called Presharding helps in this regard.
Types of Partitioning
There are two types of partitioning available in Redis. Suppose we have four Redis instances, R0, R1, R2, R3 and many keys representing users like user:1, user:2, … and so forth.
Range Partitioning
Range partitioning is accomplished by mapping ranges of objects into specific Redis instances. Suppose in our example, the users from ID 0 to ID 10000 will go into instance R0, while the users from ID 10001 to ID 20000 will go into instance R1 and so forth.
Hash Partitioning
In this type of partitioning, a hash function (eg. modulus function) is used to convert the key into a number and then the data is stored in different-different Redis instances.
Redis Pipelining
Before knowing pipelining, first know the concept of Redis:
Redis is a TCP server which supports request/response protocol. In Redis, a request is completed in two steps:
- The client sends a query to the server usually in a blocking way for the server response.
- The server processes the command and sends the response back to the client.
What is Pipelining
Pipelining facilitates a client to send multiple requests to the server without waiting for the replies at all, and finally reads the replies in a single step.
Example
Let’s see an example of Redis pipelining. In this example, we will submit multiple commands to Redis once and Redis will provide the output of all commands in a single step.
Open Redis terminal and use the following command:
- (echo -en “PING\r\n SET sssit javatraining\r\n GET sssit\r\n INCR visitor\r\n INCR visitor\r\n INCR visitor\r\n”; sleep 10) |
- nc localhost 6379
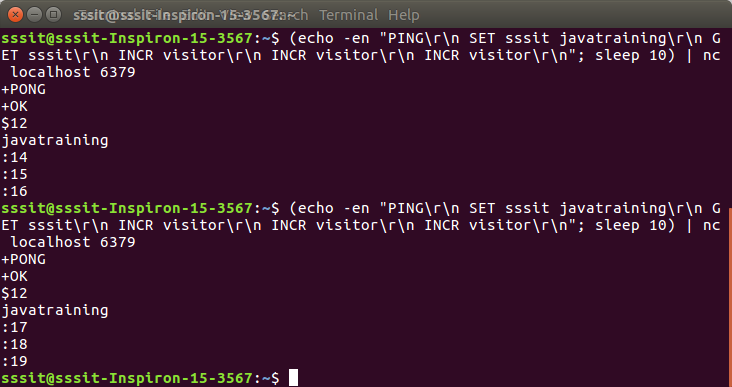
Here:
- PING command is used to check Redis connection.
- A string is set named “sssit” having a value “javatraining”.
- Got the key values and incremented the visitors numbers three times.
You can see that every time the value is incremented.
Advantage of Pipelining
The main advantage of Redis pipelining is speeding up the Redis performance. It drastically improves the protocol performance because of multiple commands simultaneous execution.
Pipelining vs Scripting
Redis Scripting is available in Redis version 2.6 or greater. A lot number of use cases for pipelining can be addressed more efficiently using scripts that perform a lot of the work needed at the server side.
The main advantage of scripting is that it can both read and write data with minimal latency. It makes operations like read, compute, write very fast.
On the other hand, pipelining doesn’t use this scenerio. In pipelining, the client needs the reply of the read command before it can call the write command.
Limitations of Redis
Let’s have a look at some of the major challenges that one might face while using Redis:
1. Basic level of security: Redis only provides basic security (such as access rights) at the instance level. The RDBMS provides detailed, per-object access control lists (also known as role management).
2. Redis, a data structure server: In Redis, there is no query language, there are only commands. Nor is there any support for the relational algebra. One cannot submit any ad-hoc queries. All of the data accesses must be anticipated by a developer, and the proper data access paths should be designed. Due to this a lot of flexibility is believed to be lost.
3. Redis, an in-memory store: All of the data must fit into the memory. The RDBMS generally stores the information on disks and the cache part of the data in the memory. By using an RDBMS, one can manage more data than the memory which one has. This is not possible with Redis.
4. Redis has only 2 options for persistence: The regular snapshotting and the append-only files. None of these are as secure as the real transactional server offering redo/undo logging, point-in-time recovery, block checksumming, flashback capabilities, etc.
5. Needs Client Support – The clients are required to make the changes in order to support the Redis Clusters. The Redis Clusters have been around for a long time now, but there are still certain clients which do not support it.
6. Supports Only a single Database – Unlike the standalone databases, the Redis Clusters support only a single database (database 0). The SELECT command is not allowed in Redis.
7. The instance is not scalable – A unique Redis instance is not said to be scalable. It only operates on one CPU core in the single-threaded mode. In order to get scalability, a number of Redis instances need to be deployed and started. The distribution and sharing are done on the client-side (a developer needs to take care of these aspects). If one compares them to a unique Redis instance, most of the RDBMS offer more scalability. It provides parallelism at the connection level. They are said to be multi-processed (such as Oracle, PostgreSQL.) or even multi-threaded (such as MySQL, Microsoft SQL Server,), deriving benefits of the multi-core machines.
Redis Advantages
There are a lot of advantages of using Redis in your application. I’ve listed them below.
- Redis allows storing key and value pairs as large as 512 MB. You can have huge keys and values of objects as big as 512 MB, which means that Redis will support up to 1GB of data for a single entry.
- Redis uses its own hashing mechanism called Redis Hashing. Redis stores data in the form of a key and a map, i.e. string fields and string values. For example, the following code uses Redis hash to save user details:
Map<String, String> user = new HashMap<>();
user.put("username", "john123");
user.put("firstName", "John");
// use Jedis clientjedis.hmset("user:john123", user);
- Redis offers data replication. Replication is the process of setting up master-slave cache nodes. The slave nodes always listen to the master node, which means that when the master node is updated, slaves will automatically be updated, as well. Redis can also update slaves asynchronously.
- The Redis cache can withstand failures and provide uninterrupted service. Since Redis can be used to set up efficient replication, at any point in time, the cache service will be up-and-running — even if any of the slave nodes are down. However, the nodes are resilient and will overcome the failure and continue providing service.
- Redis has clients in all the popular programming languages. Redis has client APIs developed in all the popular languages such as C, Ruby, Java, JavaScript, and Python.
- Redis offers a pub/sub messaging system.You can develop a high-performing messaging application using the Redis pub/sub mechanism using any language of your choice.
- Redis allows inserting huge amounts of data into its cache very easily.Sometimes, it is required to load millions of pieces of data into the cache within a short period of time. This can be done easily using mass insertion, a feature supported by Redis.
- Redis can be installed in Raspberry Pi and ARM devices. Redis has a small memory footprint and it can be installed in Raspberry Pi to enable IoT-based applications.
- Redis protocol makes it simple to implement a client. A Redis client communicates with its server using RESP (Redis Serialization Protocol). This protocol is simple to implement and is human-readable.
- Redis support transactions. Redis supports transactions, which means that commands can be executed as a queue instead of executing one at a time. Typically, commands after MULTI will be added to a queue and once EXEC is issued, all the commands saved in the queue will be executed at once.
-Redis is an open source (BSD licensed), in-memory data structure store, used as database, cache and message broker. It supports data structures such as strings, hashes, lists, sets,sorted sets with range queries, bitmaps, hyperlog logs and geospatial indexes with radius queries. Redis has built-in replication, Lua scripting, LRU eviction, transactions and different levels of on-disk persistence, and provides high availability via Redis Sentinel and automatic partitioning with Redis Cluster.
Redis is owned by Redis (www.redis.io/) and they own all related trademarks and IP rights for this software.
Redis provides a different range of persistence options:
- The RDB persistence performs point-in-time snapshots of your dataset at specified intervals.
- the AOF persistence logs every write operation received by the server, that will be played again at server startup, reconstructing the original dataset. Commands are logged using the same format as the Redis protocol itself, in an append-only fashion. Redis is able to rewrite the log on background when it gets too big.
- If you wish, you can disable persistence at all, if you want your data to just exist as long as the server is running.
- It is possible to combine both AOF and RDB in the same instance. Notice that, in this case, when Redis restarts the AOF file will be used to reconstruct the original dataset since it is guaranteed to be the most complete.
- Cognosys Provides Hardened images of Redis on the cloud ( AWS marketplace, Azure and Google Cloud Platform).Deploy Redis securely on cloud i.e. AWS marketplace, Azure and Google Cloud Platform (GCP)
Secured Redis on Ubuntu 14.04 LTS
Features
Key Features of Redis:
1. High-Level of Data Structures – Redis offers five possible data options for the values. These are hashes, lists, sets, strings, and sorted sets. The operations which are unique to these data types are given and come along with the well-documented time-complexity (The Big O notation).
2. Efficient Performance – Because of its in-memory nature, a project manager’s commitment to ensuring that complexity stays at the bare minimum, as well as an event-based programming model, the application boasts of having an exceptional performance for the read and write operations.
3. Extremely Lightweight and No Dependencies –Redis is written in the ANSI C language, and it has limited to no external dependencies. The program works perfectly well in all the POSIX environments. The Windows platform is not officially supported for Redis, but an experimental build has been provided by Microsoft for the same.
4. High Availability – Redis has Built-in support for non-blocking, asynchronous, master/slave replication, in order to ensure high-level data availability. Presently there is a high-availability solution named as the Redis Sentinel which is currently usable, but it is still considered to be a work in progress project.
5.Super-fast speed – Redis is blazingly fast! This is due to the fact that it has been written in the C language.
6.NoSQL Database – Redis is a NoSQL Database.
7. Popular usage – Presently Redis is being used by a number of tech giants such as Pinterest, Snapchat, GitHub, Weibo, Digg, StackOverflow, Craigslist and Flickr to name a few.
8. Useful for Caching – In order to protect the cloud database calls and thus save some dollars out there, one can opt for caching through the Redis.
9 Developer friendly – Redis is developer-friendly. It is presently being supported by most of the languages. This is a great advantage of using this Open Source Technology. The languages such as C, C++, C#, JavaScript, Java, Go, Objective-C, Python, PHP and almost all of the famous languages out there have support for Redis.
-Major Features Of Redis
- The full list of commands implemented by Redis, along with thorough documentation for each of them.
- Pipelining: Learn how to send multiple commands at once, saving on round trip time.
- Redis Pub/Sub: Redis is a fast and stable Publish/Subscribe messaging system! Check it out.
- Redis Lua scripting: Redis Lua scripting feature documentation.
- Debugging Lua scripts: Redis 3.2 introduces a native Lua debugger for Redis scripts.
- Memory optimization: Understand how Redis uses RAM and learn some tricks to use less of it.
- Expires: Redis allows to set a time to live different for every key so that the key will be automatically removed from the server when it expires.
- Redis as an LRU cache: How to configure and use Redis as a cache with a fixed amount of memory and auto eviction of keys.
- Redis transactions: It is possible to group commands together so that they are executed as a single transaction.
- Mass insertion of data: How to add a big amount of pre existing or generated data to a Redis instance in a short time.
- Partitioning: How to distribute your data among multiple Redis instances.
- Distributed locks: Implementing a distributed lock manager with Redis.
- Redis keyspace notifications: Get notifications of keyspace events via Pub/Sub (Redis 2.8 or greater).
- Creating secondary indexes with Redis: Use Redis data structures to create secondary indexes, composed indexes and traverse graphs.
Azure
Installation Instructions For Ubuntu
Note : How to find PublicDNS in Azure
Step 1) SSH Connection: To connect to the deployed instance, Please follow Instructions to Connect to Ubuntu instance on Azure Cloud
1) Download Putty.
2) Connect to virtual machine using following SSH credentials:
- Hostname: PublicDNS / IP of machine
- Port : 22
Username: Your chosen username when you created the machine ( For example: Azureuser)
Password : Your Chosen Password when you created the machine ( How to reset the password if you do not remember)
Step 2) Other Information:
1.The default installation path will be in your web root folder “/var/www/html”
2. Redis server configuration file path /etc/redis.conf
Important :
i)To start the redis server: service redis-server start Check the running status of redis server: service redis-server status
ii) To stop the redis server: service redis-server stop
iii) To test the installation of Redis, use below given command : redis-cli ping
iv) If the response output is PONG, it means Redis is running successfully.
3.Default ports:
- Linux Machines: SSH Port- 22
- Redis runs on port 6379 , it is not allowed on Public interface for security. Please allow as applicable to proper ACL
Configure custom inbound and outbound rules using this link
4. To access Webmin interface for management please follow this link
Installation Instructions For Centos
Note : How to find PublicDNS in Azure
Step 1) SSH Connection: To connect to the deployed instance, Please follow Instructions to Connect to Centos instance on Azure Cloud
1) Download Putty.
2) Connect to virtual machine using following SSH credentials:
- Hostname: PublicDNS / IP of machine
- Port : 22
Username: Your chosen username when you created the machine ( For example: Azureuser)
Password : Your Chosen Password when you created the machine ( How to reset the password if you do not remember)
Step 2) Other Information:
1.The default installation path will be in your web root folder “/var/www/html”
2. Redis server configuration files :
1. /etc/redis.conf
2. /etc/redis-sentinel.conf
Important :
i)To start the redis server: systemctl start redis.service
ii) Check the running status of redis server: systemctl status redis.service
iii) To test the installation of Redis, use below given command: redis-cli ping
iv) If the response output is PONG, it means Redis is running successfully.
3.Default ports:
- Linux Machines: SSH Port- 22
- Redis runs on port 6379 , it is not allowed on the Public interface for security. Please allow as applicable to proper ACL
Configure custom inbound and outbound rules using this link
4. To access Webmin interface for management please follow this link
Redis with CentOS – All Other Versions
Azure Marketplace – Redis with CentOS 8.2
Azure Marketplace – Redis with CentOS 7.8
Azure Marketplace – Redis with CentOS 7.7
Azure Marketplace – Redis with CentOS 7.6
Azure Marketplace – Redis with CentOS 7.5
Installation Instructions For Redhat
Step 1) VM Creation:
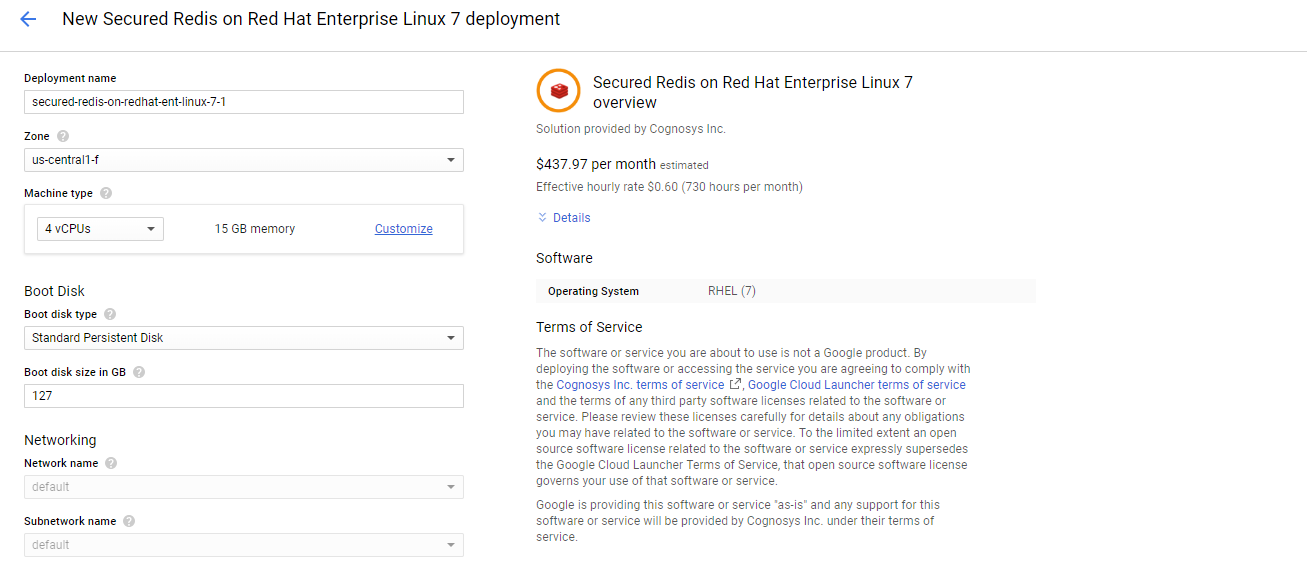
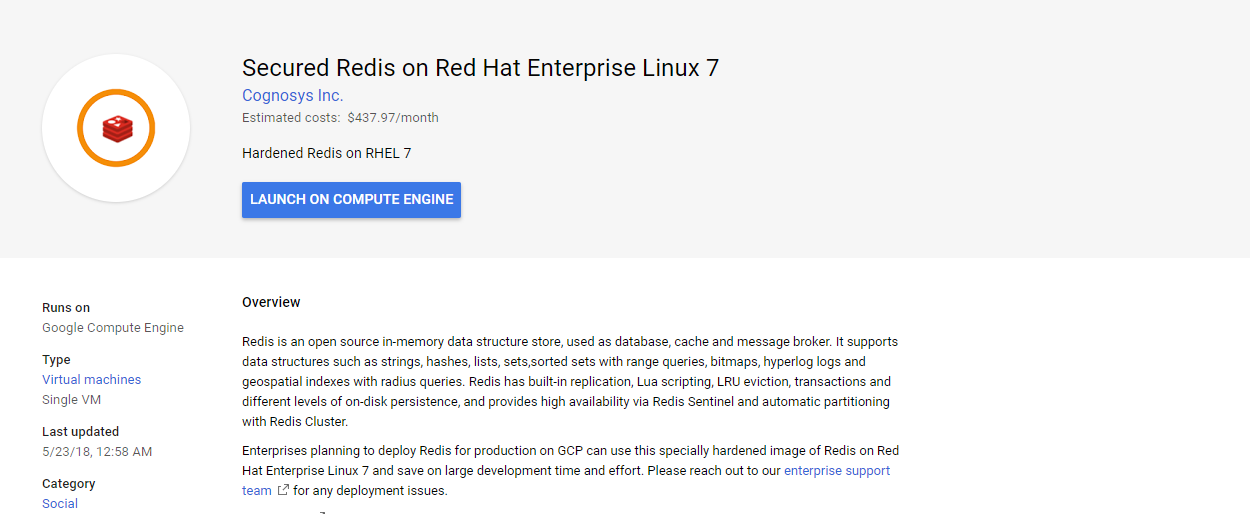 2.You can see at this page, an overview of Cognosys Image as well as some estimated costs of VM.
2.You can see at this page, an overview of Cognosys Image as well as some estimated costs of VM.
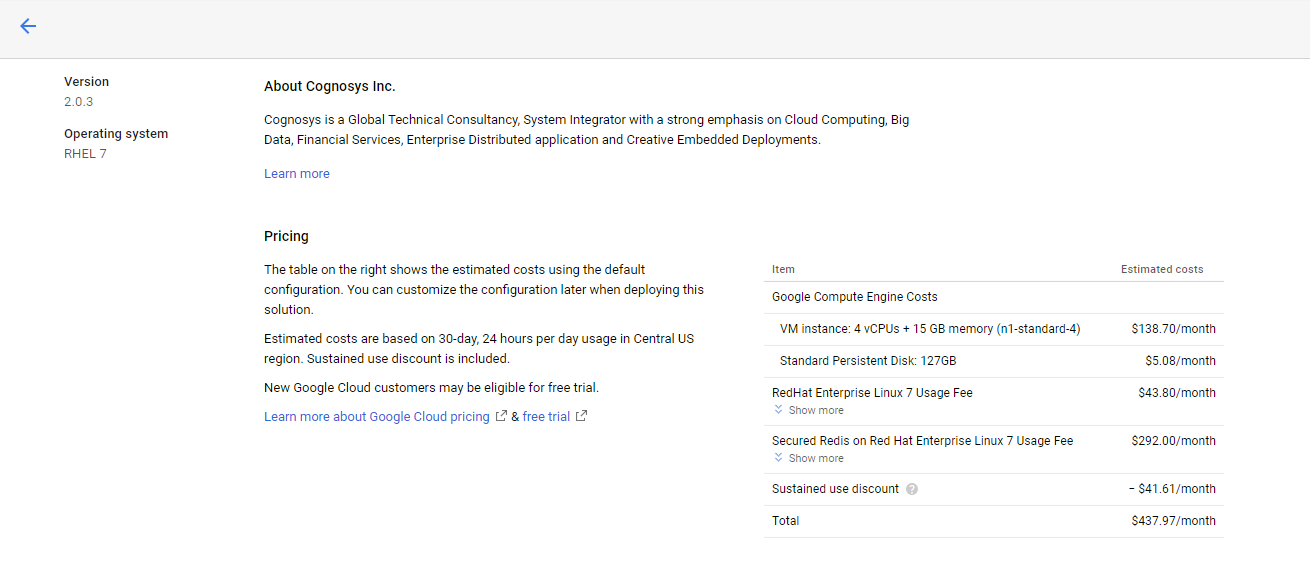 3.In the settings page, you can choose the number of CPUs and amount of RAM, the disk size and type etc.
3.In the settings page, you can choose the number of CPUs and amount of RAM, the disk size and type etc.
Step 2) SSH Connection: To connect to the deployed instance, Please follow Instructions to Connect to Redhat instance on Google Cloud
1) Download Putty.
2) Connect to the virtual machine using SSH key
- Hostname: PublicDNS / IP of machine
- Port : 22
Step 3) Other Information:
1.The default installation path will be in your web root folder “/var/www/html”
2. Redis server configuration files :
1. /etc/redis.conf
2. /etc/redis-sentinel.conf
Important :
i)To start the redis server: systemctl start redis.service
ii) Check the running status of redis server: systemctl status redis.service
iii) To test the installation of Redis, use below given command: redis-cli ping
iv) If the response output is PONG, it means Redis is running successfully.
3.Default ports:
- Linux Machines: SSH Port- 22
- Redis runs on port 6379 , it is not allowed on the Public interface for security. Please allow as applicable to proper ACL
Configure custom inbound and outbound rules using this link
4. To access Webmin interface for management please follow this link
Videos
Secured Redis on Ubuntu 14.04 LTS
What is Redis?
Top Uses of Redis
Installing Redis on linux/ ubuntu


