1-click AWS Deployment 1-click Azure Deployment
Overview
Process Hacker is a free and open source app that allows you eyesight all the procedures that your system runs. The app is a powerful multi-purpose tool that can be used as a replacement for Windows Task Manager. It will help you with debugging, malware detection and system monitoring. Process Hacker includes features like powerful process termination, memory viewing/editing and other exceptional and expert features. Process Hacker is a graphical tool for managing 32-bit and 64-bit Microsoft Windows processes, services, threads, memory, handles, modules, Security Access Tokens (SATs) and network connections. It is a wonderful tool for analyzing and combating malware, understanding low-level details of the Windows operating system, troubleshooting, and experimenting with Windows in ways which Microsoft never intended.
Process Hacker gives you a detailed overview of your system activity by highlighting the processes in different colours. You can also view your system resources by means of graphs and stats.
Key Features Include:
- Powerful process termination features.
- Thorough system information and graphs.
- Clear overview of running processes and resource usage.
- View and edit services.
- Bypasses security software and root-kits.
- Debugging and data analyzing support.
Process Hacker also allows you to copy data and shows you symbolic access masks. The app is customizable and open source, so you can modify it and redistribute it. Overall, the app has an easy to navigate user interface that is coupled with many powerful features. If you use Windows Task Manager regularly, then you really should consider using this as an alternative.
Process Hacker Tool for Manipulating System Services and Processes
Windows operating system contain services and processes, some of them are required for certain tasks or operations other consume the memory without any usage and some are on the system with a malicious intent.
To detect and resolve what you are running on your system you can consider Process Hacker very useful tool that will make your system naked, all you need to do is executing the program on the system you need to analyzer and you will have the following:
1– Process Information and functionality:
You can list processes with (process ID, CPU consumption, user name and a short description of the process) by selecting the process and clicking on right mouse button you can terminate, suspend, and restart the process.
You can open process file location , search the process name online to check more information directly from the tool, it is also possible to send it for several online services such as Virus total , jotti.org or comodo without making any complicated actions.
2– Service information and functionality:
Here you can have list of services running on the system and you can stop certain services as you need.
3- Network information and functionality
On the network tab you can find list of application or services running with type of protocol in use and local port with status if it is in wait for connection or not.
Process Hacker is very important tool if you are looking to conduct a dynamic malware analyses with sandboxing as you can have a virtual box with several version of operating system and execute the malware next you check what changes in the system before and after execution.
Process Hacker shows a detailed overview of system activity and supports process highlighting. It can also display graphs and statistics to help you locate processes that use the most memory and find runaway processes. You can also double click the graph to see more information about the process at that data point, even if the process is no longer running.
If you encounter a file that you are unable to edit or delete, Process Hacker allows you to search for and discover which handles or DLLs are using that file and restricting access to it. After running your search and finding which processes are using that file, you can simply right click the entry and close the handle. As always, proceed with caution when closing the handle as this can lead to data loss or corruption.
Another useful module in Process Hacker is the ability to see which programs have active network connections and the ability to close them if required. Included with this information is the local port, remote address, remote port, protocol, state and the owner.
Process Hacker can also display real-time information on disk access, which includes the read and write speeds, the total rate, I/O priority and more. By right clicking one of the actions shown in the disk activity section, you have the ability to go directly to the process, open the file location, copy the information displayed or view properties of that file.
Process Hacker has even more advanced features that have not been listed here, but are displayed on the developer’s homepage with fully detailed screenshots.
Installing
If you just want to start using the tool it’s as easy as downloading and running the installer:

During the installation process you will see a few options



Select the components you wish. They don’t require a lot of space, so there is no need to be picky.

These are worth studying and depend on how you plan to use Process Hacker. Most can be changed afterwards though.

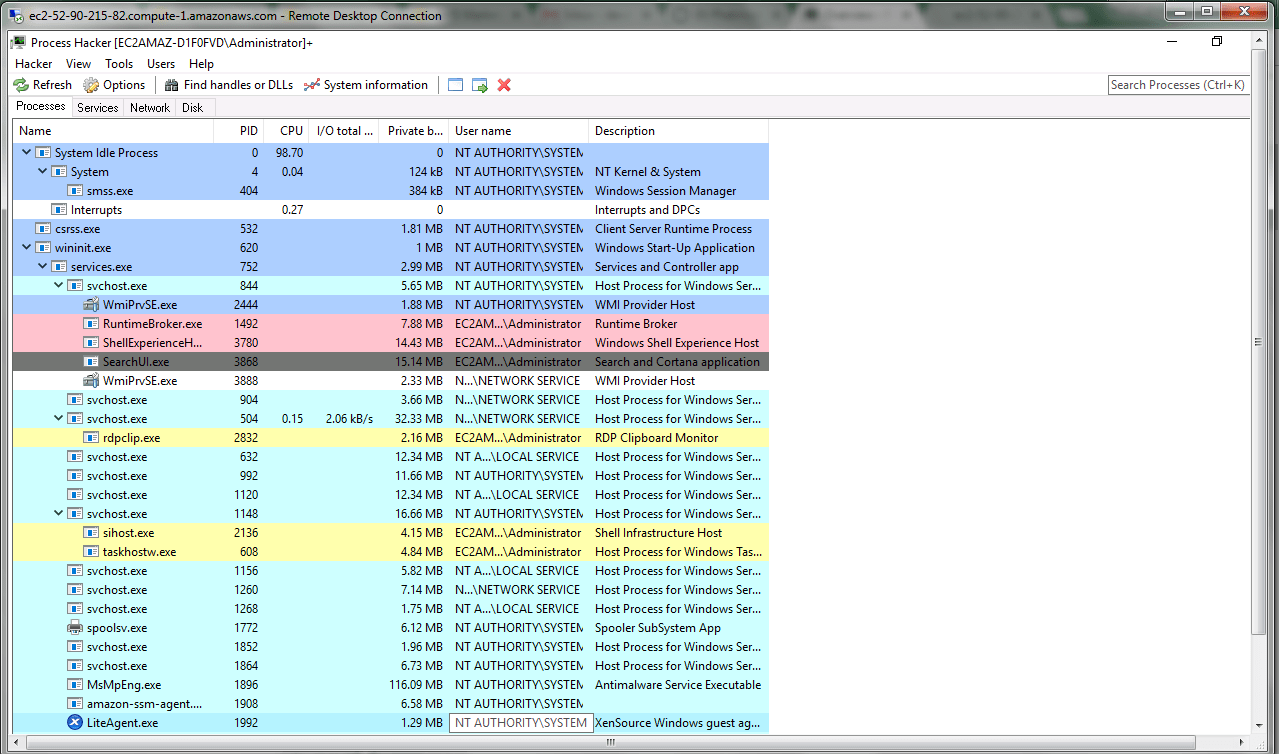
The main screen
When you run Process Hacker this is the main screen.

In the default settings it shows you the Processes tab with all the running processes in tree-view and lists:
their Process Identifier (PID)
their CPU usage percentage (CPU)
their I/O total rate
their private bytes
the user-name the process is running under
a short description
By hovering over one of the process name you can find more information about them

The other tabs are Services, Network, and Disk. Each of the last two shows more information about the processes with regards to their network and disk usage respectively. The services tab shows a full list of present services and drivers.

The meaning of the color-coding of the processes can be found, and changed, under Hacker > Options > on the Highlighting tab.

The option to toggle to Replace Task manager with Process Hacker can be found under Hacker > Options > on the Advanced tab.
Process Hacker can help you identify that process and break the tie. Here’s the procedure:
1 In the main menu click on Find handles or DLLs
2 In the Filter bar type the full name of the file or a part of that name, then click on Find
3 In the results look for the exact filename and right-click that line
4 From the right-click menu choose Go to owning process
5 The process will be highlighted in the Processes window
6 Right-click the highlighter process and choose Terminate
7 Consider the warning in the prompt that data might be lost and be aware that Process Hacker can close processes where other task managers might fail
8 If you choose to terminate the process you can try deleting the locked file again
Escaping browlocks
Process Hacker can also help you to escape some of the sites that use browlock tactics. For example sites that use this login script:

The goal of the threat-actors is is to get the visitor of the site to first allow notifications, and in the end, get him to install one of their extensions. Malwarebytes generally detects these extensions as PUP.Optional.ForcedInstalledExtensionFF.Generic.

Once you found the guilty party, select the line that shows the contact to the IP or domain of the browlock site. I used tracert to determine the IP for ffkeitlink.cool. Right-click that line and choose Close and this will temporarily break the connection, stopping the script from refreshing the prompt all the time. That give you the chance to close the tab and carry on without having to force-close the Firefox process.
Dumping strings from memory
You can use Process Hacker to create memory dumps of processes. Analysts use these dumps to search for strings and they use scripts or Yara rules to make an initial classification of a process. Is it malware? If so, what kind of malware? Is it after information, which information, and where does it send it?Right-click on the running process you wish to create a memory dump for and select Create dump file… and then use the explorer window to browse to the location where you want to save the dump. The memory dump created by Process Hacker will have the dmp extension. Depending on what you are looking for the dmp file can be opened in a hex editor, a text editor, or mimikatz (if you are after credentials).
Finding resource hogs
As with most programs of this kind identifying resource, hogs is easy.

Click the CPU title above the column and the column will be sorted by CPU usage, showing you if a process is slowing you down and which one. The same can be done for Private bytes and I/O total rate.
Versatile and powerful
Process Hacker is a very versatile tool that has a lot in common with Process Explorer. Since it does have a few more options and is more powerful than Process Explorer, advanced users may prefer Process Hacker. Less advanced users who are afraid of the possible consequences of the extra power might want to stick with Process Explorer. If you require help with Process Hacker they have a fairly active forum where you might find a helping hand.
Process Hacker is an open source process viewer. It is similar to Process Explorer, but has many more features for debugging and monitoring. Additionally, it can terminate processes that other tools cannot.
It is a free and open source app that will let you view all the processes that your system runs. The app is a powerful multi-purpose tool that can be used as a replacement for Windows Task Manager.
It will help you with debugging, malware detection and system monitoring. Process Hacker includes features like powerful process termination, memory viewing/editing and other unique and specialized features.
Process Hacker is owned by Process Hacker(https://wj32.org/processhacker/) and they own all related trademarks and IP rights for this software.
Process Hacker gives you a detailed overview of your system activity by highlighting the processes in different colours. You can also view your system resources by means of graphs and stats.
Process Hacker on Cloud For AWS
Features
Major Features Of Process Hacker
Process Hacker has a rich feature set which includes the following:
- One major addition is support for viewing the load time and load reasons for process modules, on Windows 8 and above. If a long-running process like Explorer.exe is developing problems, you can now sort its modules by load time to get clues about the cause.
- Priority and I/O priority can be set for multiple processes at once, while I/O priorities may be saved as required.
- Right-clicking a service now provides menu options to open its key in Regedit, or open its file location in Explorer.
- There’s new support for checking process use of Control Flow Guard, Microsoft’s new exploit mitigation technology for Windows 8.1 and 10.
- You’ll get handle names for job and section objects, while the very brave can directly access section objects in memory (double-click a process, select Handles, right-click a section, select Read/ Write Memory).
- Elsewhere there’s new highlighting for AppContainer DLLs, disk and network graphs are now available for all processes, there’s support for setting thread/ process affinity on up to 64 processors and the ExtendedTools and UserNotes plugins have both seen updates.
AWS
Installation Instructions For Windows
Note: How to find PublicDNS in AWS
Step 1) RDP Connection: To connect to the deployed instance, Please follow Instructions to Connect to Windows instance on AWS Cloud
1) Connect to the virtual machine using following RDP credentials:
- Hostname: PublicDNS / IP of machine
- Port : 3389
Username: To connect to the operating system, use RDP and the username is Administrator.
Password: Please Click here to know how to get password .
Step 2) Click the Windows “Start” button and select “All Programs” and then point to Process Hacker
Step 3) Other Information:
1.Default installation path: will be in your root folder “C:\Program Files\Process Hacker 2”
2.Default ports:
- Windows Machines: RDP Port – 3389
- Http: 80
- Https: 443
Configure custom inbound and outbound rules using this link
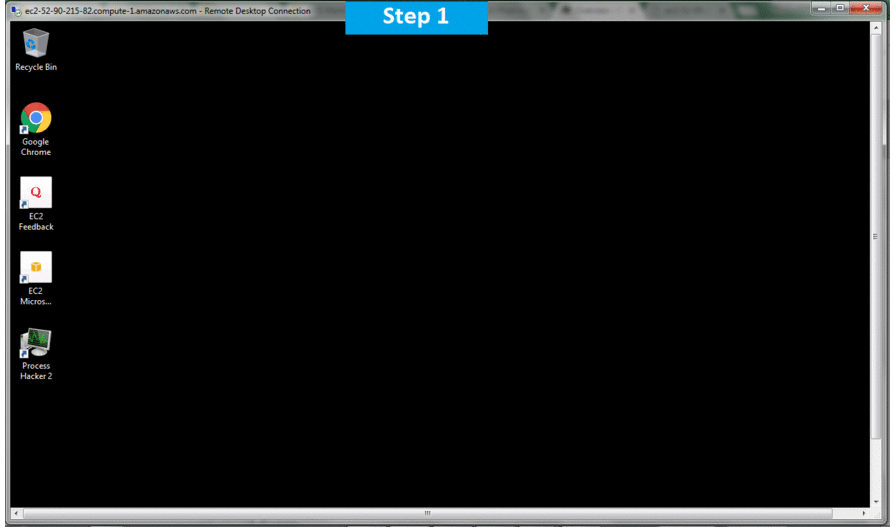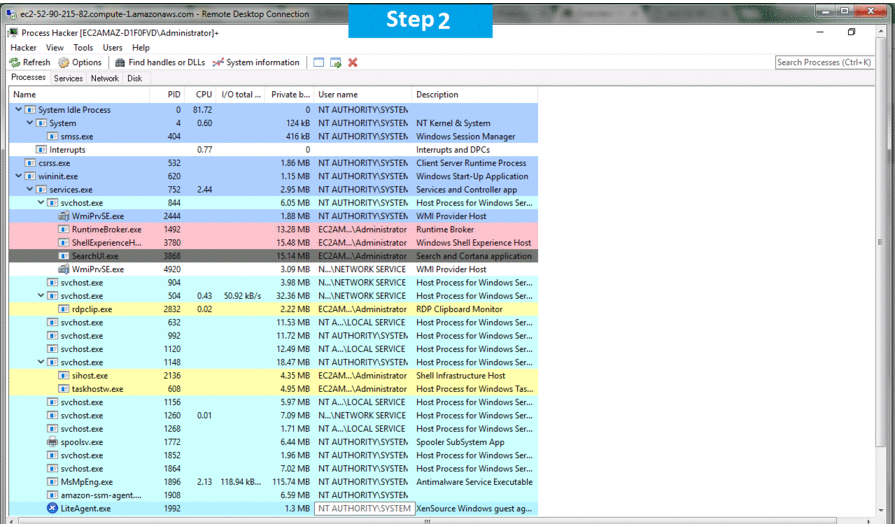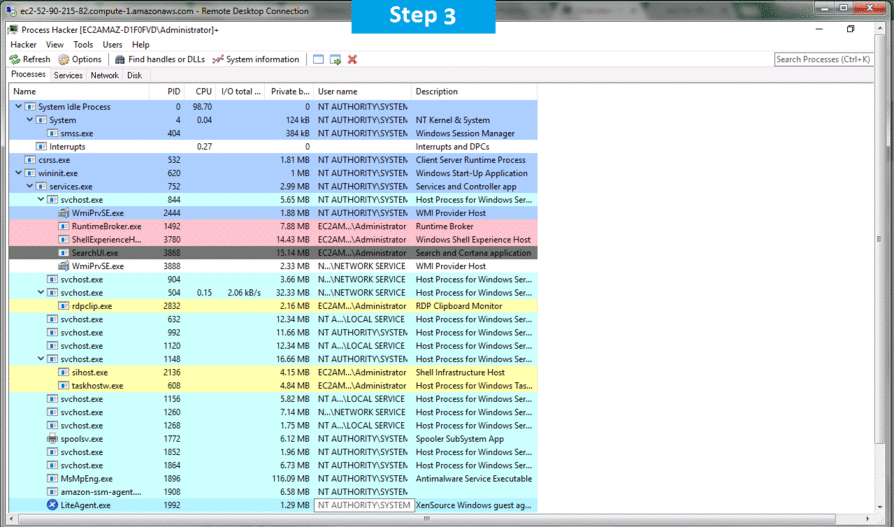
Installation Step by Sinp Screenshots