1-click AWS Deployment 1-click Azure Deployment
Overview
Eraser
Eraser is a free data-destruction program that’s capable to erase all the data off of whole hard drive at once. Since it also can forever delete individual files and folders as well, it’s also a great free file-shredder program. Eraser can be used to schedule data-wipe tasks and supports lots of refinement methods, making it a great way to escape file-recovery programs.
Deletion is never safe. Deleting a file only removes the entry of the file (pointer) from the file index in a file system. Thus, the actual data still remains on the drive and can be easily recovered with the help of a basic data recovery tool. Therefore, it’s important that you completely destroy the data from your storage devices by using a data erasure tool before disposing them off, discarding them or else donating them to someone.
Why Data Erasure Tool?
The data erasure tool such as BitRaser for File offers multiple erasure algorithms that ensure data is destroyed beyond the scope of recovery. Erasure algorithms are a set of rules and instructions or in other words – a formula to destroy the data from a memory device by overwriting it with random bits (values/characters) of data either once, twice, or several times and verifying it at the same time.
There are several data erasure algorithms that are used across the globe to completely destroy the confidential, private, and sensitive data from the memory devices such as hard drives, SSDs, SD cards, Flash drives, etc. – beyond the scope of recovery. Some of these erasure algorithms are designed by the world’s most renowned military organizations like U.S. Department of Defense, governments, and private organizations around the world. These algorithms are designed to ensure that their confidential and private files/data does not leak or land into the hands of any unauthorized entity or enemy and can’t be recovered with any commercially available process.
Eraser works by scheduling tasks to erase certain files. You can set up a task to run immediately after it has been created, manually, on every restart, or on recurring daily, weekly, or monthly schedule. So here are some of the most effective data erasure algorithms & standards that an individual or organization can use to sanitize the data and ensure privacy & data security.
Eraser can use any of these data-sanitization methods to securely remove data from a drive:
- DoD 5220.22-M
The DoD 5220.22-M sanitization method is one of the most shared sanitization methods used in data destruction software, and in general, is still apparent as an industry standard in the U.S. Most data sanitization software, including Blancco Drive Eraser, supports multiple data sanitization methods, including DoD 5220.22-M. However, in most cases, this DoD technique is now less effective, more resource demanding, and less economical than more modern standards, so it has fallen out of recommended practice even at federal agencies. Yet because even historical Department of Defense standards are held in high regard and carry great credibility, organizations’ internal policies and information security teams may still need it.
AFSSI-5020
All data sanitization methods are alike in some ways but somewhat different in others. For example, the VSITR sanitization method writes several passes of ones and zeros before finishing with a random character. Write Zero only writes one pass of zeros, while Random Data uses random characters. The AFSSI-5020 data sanitization method is similar in that it uses zeros, ones, and random characters, but different in the order and number of passes. It’s extremely similar to CSEC ITSG-06, NAVSO P-5239-26, and DoD 5220.22-M.
The AFSSI-5020 data wipe method is usually implemented in the following way:
- Pass 1: Writes a zero
- Pass 2: Writes a one
- Pass 3: Writes a random character and verifies the write
You might also see iterations of the AFSSI-5020 data sanitization method that write a one for the first pass and a zero for the second. This method has also been seen implemented with verifications after each pass, not just the last one.
Some applications that support AFSSI-5020 may let you modify the passes to make your own custom data wipe method. For example, you might be able to replace the first pass with random characters and end it with a verification.
Though, remember that specific changes made to this sanitization method may result in a method that’s technically no longer AFSSI-5020. For example, if you made the first three passes random characters instead of ones or zeros, and then added several more passes, you could build the Gutmann method. Similarly, deleting the last two passes would leave you with Write Zero.
Programs That Support AFSSI-5020
Eraser, Hard Disk Scrubber, and PrivaZer are a few free programs that let you use the AFSSI-5020 data sanitization method. Eraser and PrivaZer can overwrite data on a whole storage device at once using this sanitization method while Hard Disk Scrubber is only useful for securely deleting select files and folders, not entire hard drives.
These programs, and most others that support this data wipe method, also support multiple other data sanitization methods in addition to AFSSI-5020. This is helpful because it means you can use a different sanitization method later if you want, or even use multiple methods on the same data, without having to switch to a different application.
AR 380-19
The US Army AR 380-19 data erasure method is defined & published by the US Army in the Army Regulation 380-19. This data erasure algorithm destroys the data in 3 passes as mentioned below:
- Pass 1: It writes random character
- Pass 2: Writes specified character on the drive (E.g. One)
- Pass 3: Overwrites the complement of specified character i.e. Zero and then it verifies overwrites
RCMP TSSIT OPS-II
This data sanitization algorithm was defined by the Royal Canadian Mounted Police (RCMP). It uses 6 passes of complementary repeated values and ends by overwriting a pseudo-random character with verification in 7th pass.
- Pass 1: overwrites a fixed value (e.g. zero)
- Pass 2: Overwrites complement of Pass 1 (i.e. one)
- Pass 3: Overwrites complement of Pass 2 (zero)
- Pass 4: Overwrites complement of Pass 3 (one)
- Pass 5: Overwrites complement of Pass 4 (zero)
- Pass 6: Overwrites complement of Pass 5 (one)
- Pass 7: Overwrites a pseudo-random value and verifies the write
Unlike DoD 5220.22-M that verifies overwrite after each overwrite, this algorithm verifies overwrite in the 7th pass only.
HMG IS5
HMG IS5 erasure standard uses 2 passes or 3 passes where it writes combination of Zero, One, & Random data with verification. British HMG IS5 3 pass is much more enhanced than the 2 passes.
2 pass British HMG IS5:
- Pass 1: Writes Zero
- Pass 2: Writes Random data and verifies it
3 Pass British HMG IS5
- Pass 1: Writes Zero
- Pass 2: Writes One
- Pass 3: Writes Random data and verifies it
VSITR Wipe Method
There are several different data sanitization methods supported by various applications but all of them use either ones, zeros, random data, or a combination of all three. VSITR is one example of a data wipe method that utilizes all three.For example, Write Zero just writes zeros over the data and Random Data uses random characters, but VSITR acts sort of as a combination of both of those methods.
This is how the VSITR data sanitization method is most often implemented:
- Pass 1: Writes a zero
- Pass 2: Writes a one
- Pass 3: Writes a zero
- Pass 4: Writes a one
- Pass 5: Writes a zero
- Pass 6: Writes a one
- Pass 7: Writes a random character
VSITR implemented this way makes it identical to the RCMP TSSIT OPS-II data sanitization method except that VSITR lacks any verification.
A verification is just a way for the program to double-check that the data was actually overwritten. Usually, if the verification fails, the program will repeat the pass until it passes.
We’ve seen various other VSITR iterations as well including one with only three passes, one that writes the letter A in the final pass instead of a random character, and one that writes alternating ones and zeros across the entire drive as the last pass.
Some file shredders and data destruction programs let you customize the data sanitization method. However, if you make certain changes to a wipe method, you’re basically using a different one altogether. For example, if you customize VSITR to include a verification after the last pass, you’re now using the RCMP TSSIT OPS-II method.
Programs That Support VSITR
File shredders are programs that use a data sanitization method to securely erase specific files and folders of your choosing. Eraser, Secure Eraser, and Delete Files Permanently are some examples of file shredder tools that support the VSITR data wipe method.If you’re looking for a data destruction program that will overwrite all the existing data on an entire storage device using the VSITR data sanitization method, CBL Data Shredder, Hardwipe, and Free EASIS Data Eraser are a few. The Eraser and Secure Eraser file shredder applications mentioned above can also be used to erase hard drives using VSITR.Most data destruction programs and file shredders support multiple data sanitization methods in addition to VSITR. This means even if you install the program to use it for VSITR, you can most likely choose a different data wipe method later or even use more than one method on the same data.
GOST R 50739-95 Wipe Method
The GOST R 50739-95 data sanitization method is usually implemented in one of these two ways:
First version:
- Pass 1: Writes a zero
- Pass 2: Writes a random character
Second version:
- Pass 1: Writes a random character
One major difference between the GOST R 50739-95 method of erasing data when compared with others, is that it’s not a requirement for there to be a “verification” pass after the information has been overwritten.
All this means is that the program using the wipe method can still claim to have used GOST R 50739-95 even if it doesn’t double-check that the data was actually cleared away.
However, any program using GOST R 50739-95 can verify the overwrite if it chooses to; this is usually an option in data destruction programs and file shredders.
Free Software That Support the GOST R 50739-95 Method
There are plenty of free applications that can use a specific data wipe method to overwrite files and make it much harder, if not impossible, to recover by the average person. A few of these supports the GOST R 50739-95 method, but before deciding, first identify what you want to delete and how you plan on deleting it.
For example, if you just need a simple file shredder that can delete specific files and not necessarily entire folders or hard drives at once, Delete Files Permanently is one that supports GOST R 50739-95. So too can Eraser and Hardwipe.
The latter two, plus Disk Wipe, are useful if you do need to erase all the files in a folder or erase every single piece of data from an external hard drive like a flash drive, or another internal hard drive.
However, you need to take a whole different approach if you plan to erase all the files on your primary hard drive; the one that you’re using right now. This is because you cannot run software on the same hard drive that you want to erase.
For that, you need a data wipe program that runs before the operating system starts. That is, one that you can boot to from a flash drive or disc instead of your primary hard drive. That way, you can erase every single file that would normally be locked or in use while the hard drive is active.
CBL Data Shredder is one example of such a program. However, unlike the tools mentioned above, this one doesn’t include GOST R 50739-95 as a default option. Instead, you must customize the passes to make the first one writes zeros over the data and the second write random characters.
Most data destruction programs support multiple data sanitization methods in addition to GOST R 50739-95. This means you can use the same software to utilize the DoD 5220.22-M, Gutmann, and Random Data methods, for example.
Hard Disk Scrubber is another tool that can overwrite individual files using the GOST R 50739-95 method, but you have to build the custom passes yourself like with what’s required with CBL Data Shredder
Gutmann
- The Gutmann method uses a random character, instead of just the zero used in other techniques, for the first 4 and the last 4 passes, but then uses a complex pattern of overwriting from Pass 5 through Pass 31. It writes a total of 35 passes.There is a lengthy explanation of the original Gutmann method, which includes a table of the patterns used in each pass.
- Is Gutmann Better Than Other Erase Methods?
- The regular delete operation in your average operating system isn’t sufficient for securely erasing files, because it just marks that file space as being empty so that another file can take its place. No file recovery program would have a problem resurrecting the file.
- The market supports several different data sanitization methods you could use instead, such as DoD 5220.22-M, Secure Erase, or Random Data, but each of them is different in one way or another from the Gutmann method. The Gutmann method differs from these other methods in that it performs 35 passes over the data instead of just one or a few. The obvious question, then, is whether the Gutmann method should be used over the substitutes. The Gutmann method was designed in the late 1900s. The hard drives in use at that time used different encoding methods than the ones we use today, so most of the passes the Gutmann method performs are completely useless for modern hard drives. Without knowing exactly how each hard drive stores data, the best way to erase it is to use random patterns.
This version of Eraser supports Windows 8, Windows 7, Windows Vista, Windows XP, and Windows Server 2003-2012. It works well in Windows 10. Eraser must be installed on your computer to use it. This means you can’t erase your primary hard drive — the one that’s running Windows. For example, if you’re using Eraser in Windows 8, you can’t use it to remove all the Windows 8 files. For that, you must use a program that runs before the operating system is launched. See our article on How to Wipe a Hard Drive for more on that. However, you can use Eraser against an external drive, any other internal drive, or any single or group of files/folders.
Eraser is an advanced security tool for Windows which allows you to completely remove sensitive data from your hard drive by overwriting it several times with carefully selected patterns.
When you delete a file, the operating system does not really remove the file from the disk; it only removes the reference of the file from the file system table. The file remains on the disk until another file is created over it, and even after that, it might be possible to recover data by studying the magnetic fields on the disk platter surface.
There are several problems in secure file removal, mostly caused by the use of write cache, construction of the hard disk and the use of data encoding. These problems have been taken into consideration when Eraser was designed, and because of this intuitive design and a simple user interface, you can safely and easily erase private data from your hard drive.
Eraser is owned by Eraser(https://eraser.heidi.ie/) and they own all related trademarks and IP rights for this software.
Eraser on cloud for AWS
Features
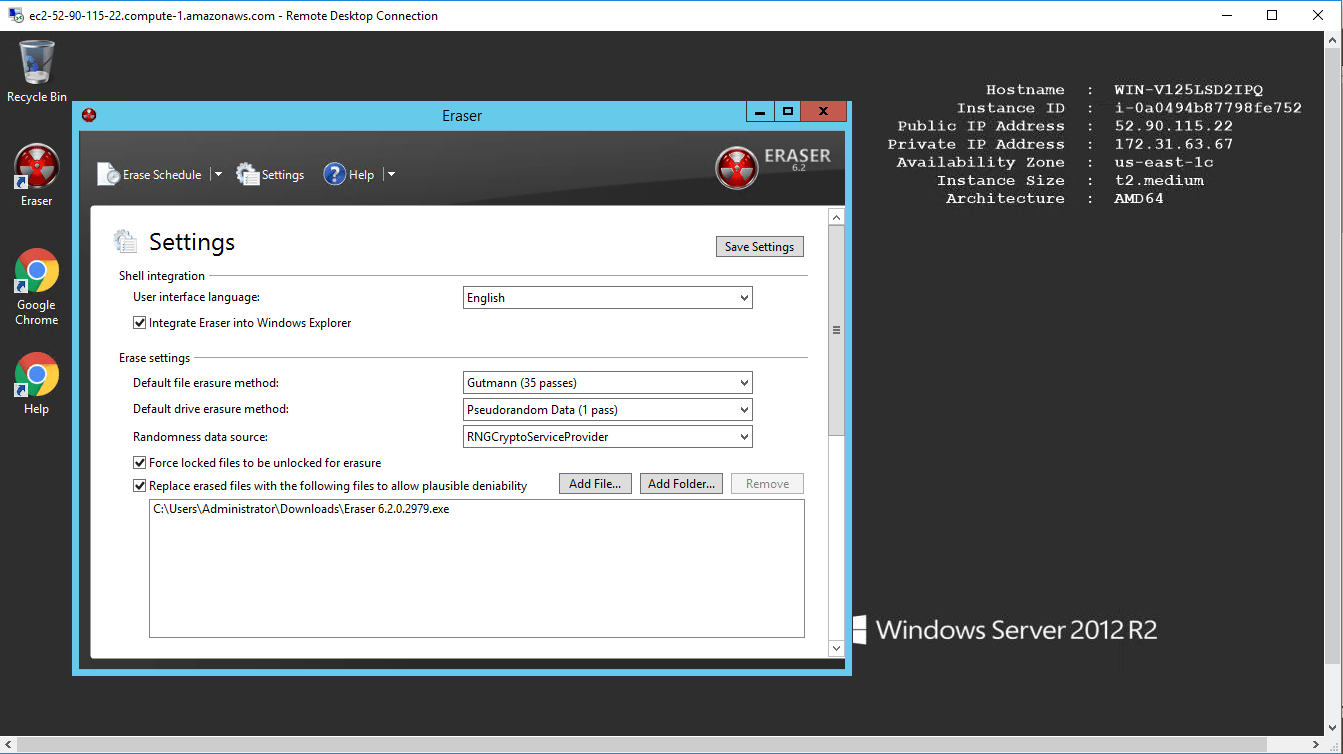
Some great features and functionality of this software are as follows:
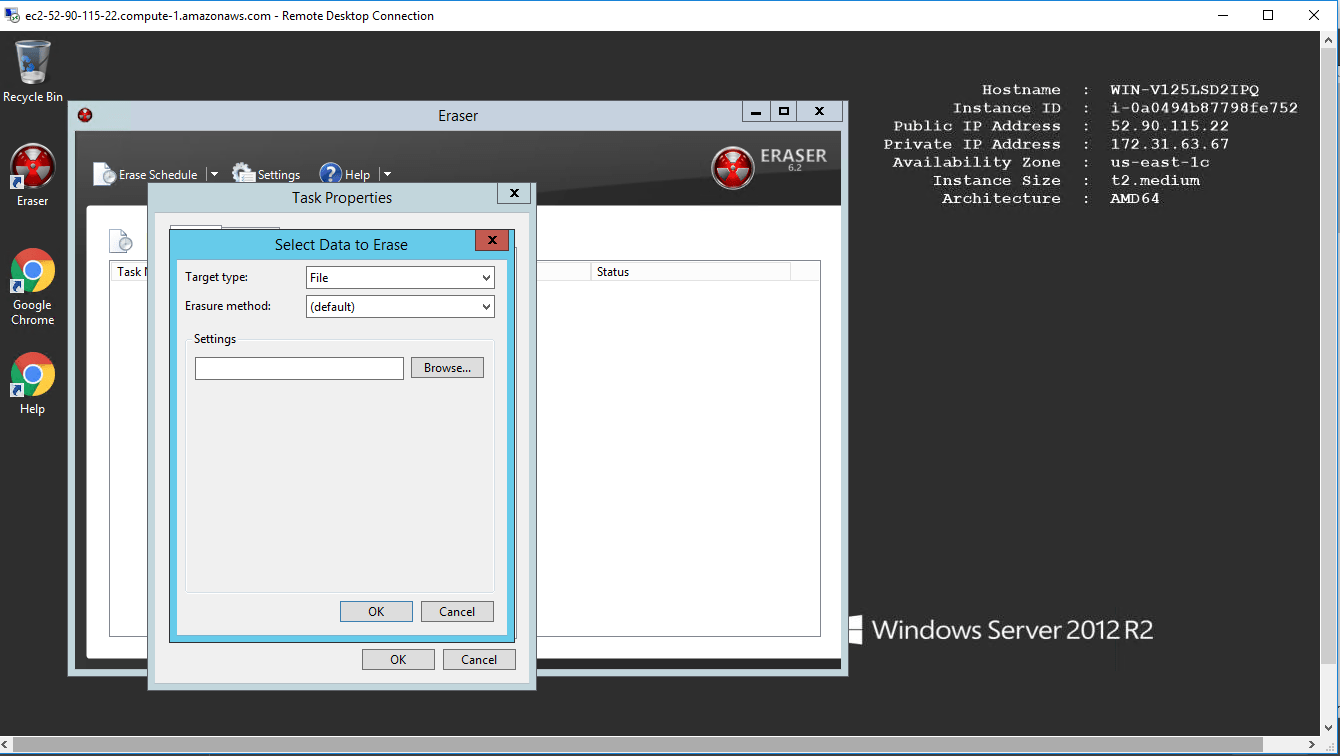
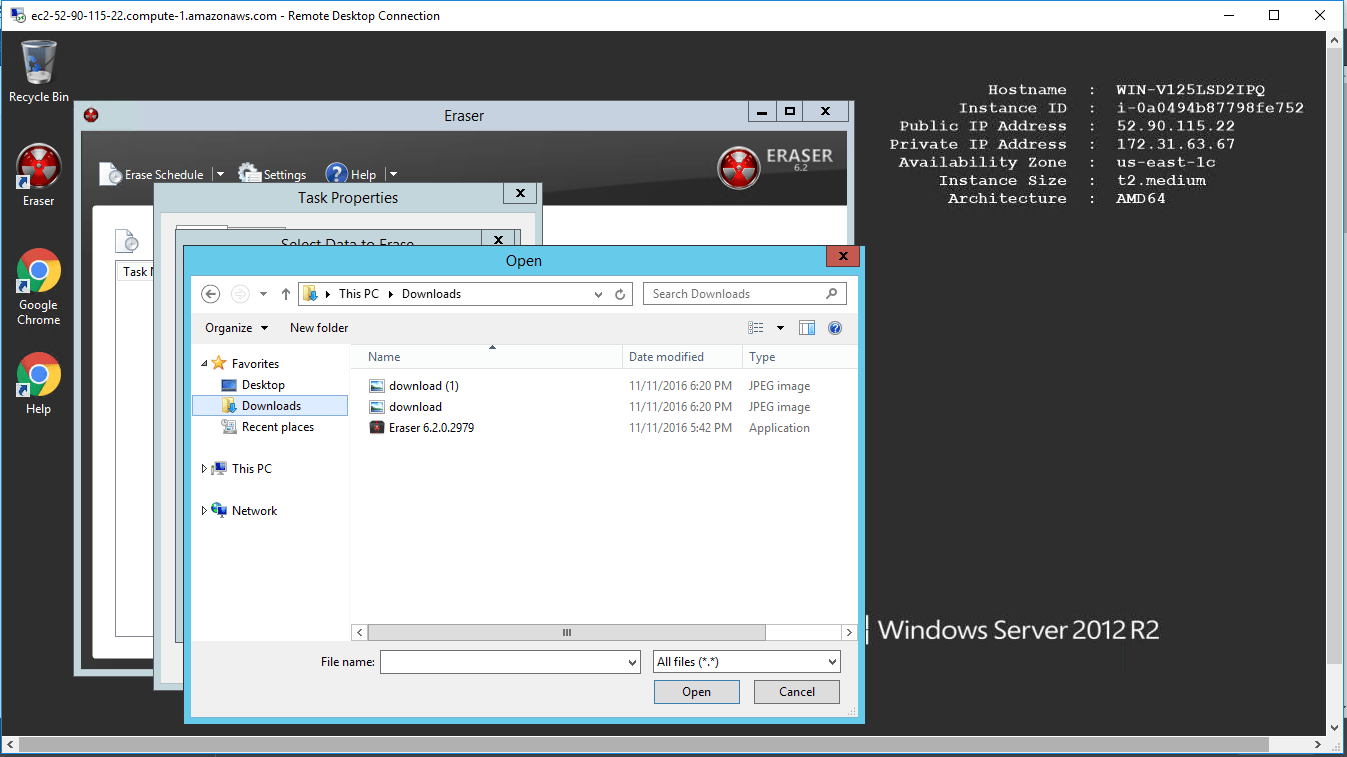
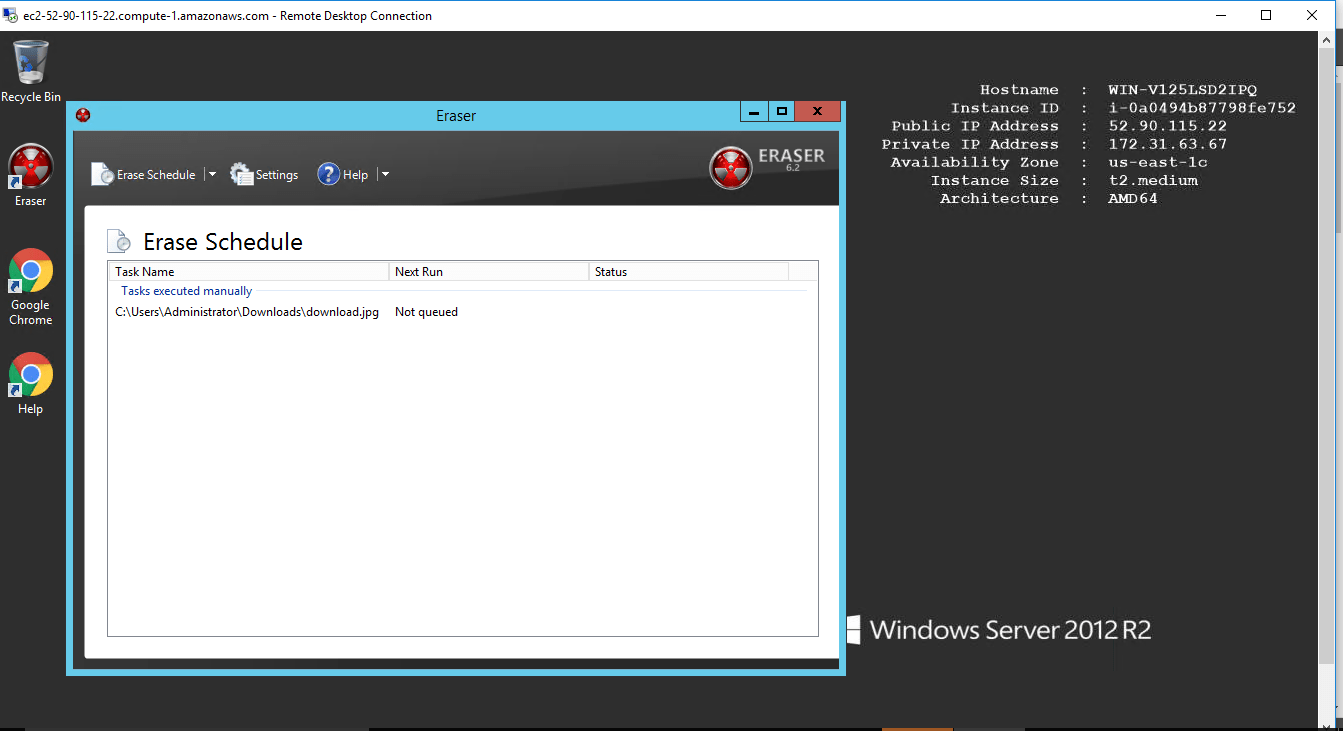
- Creating Tasks
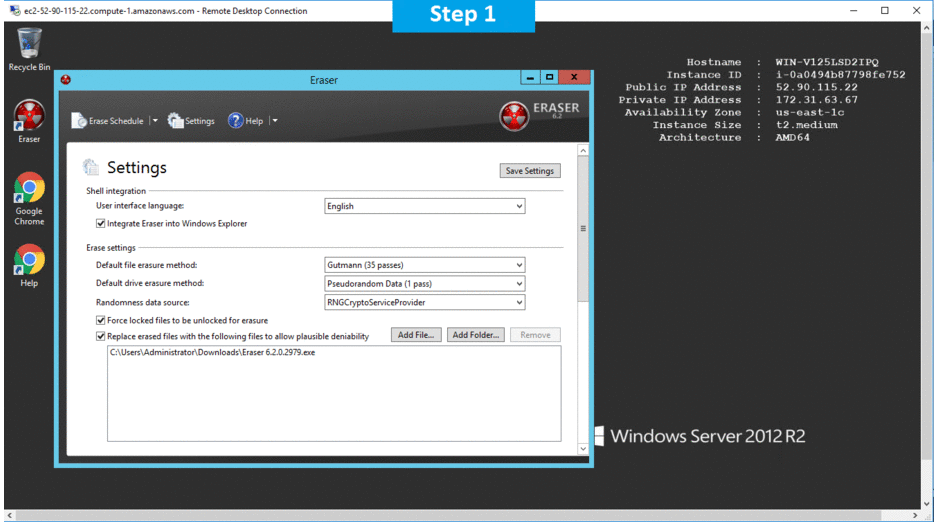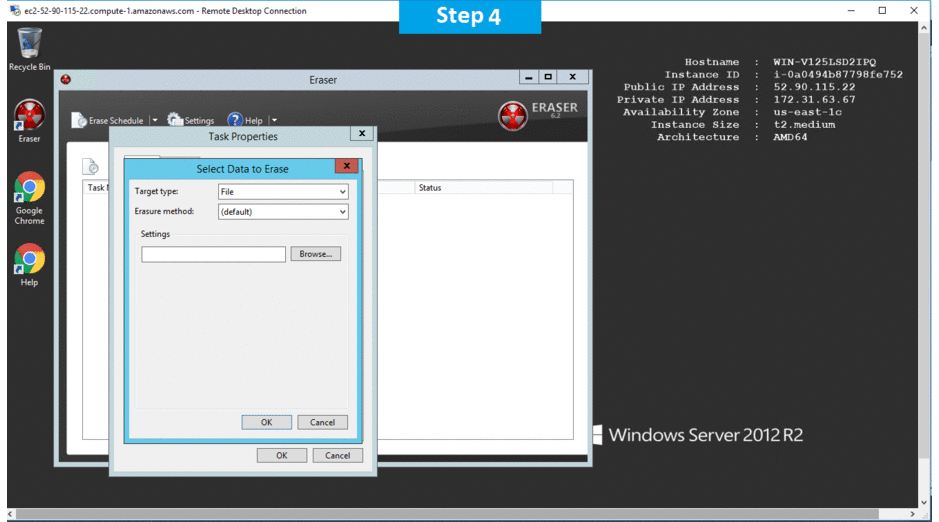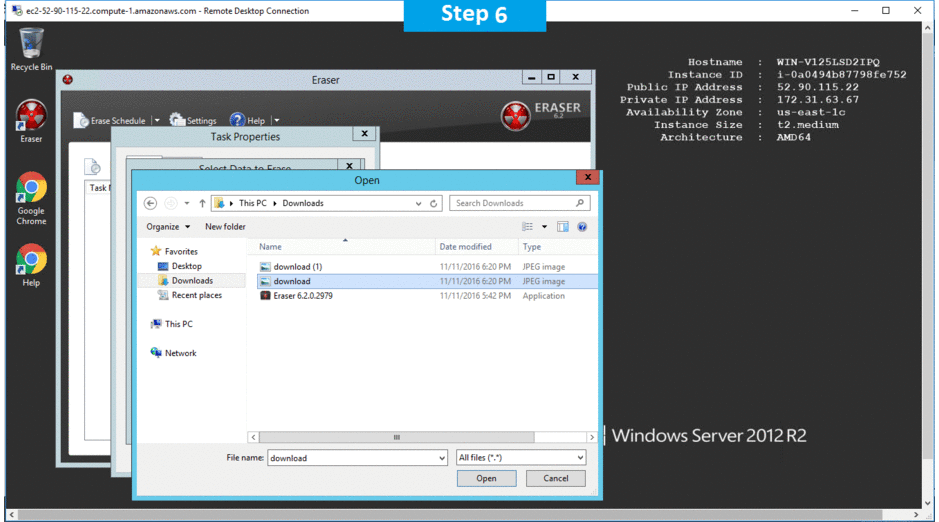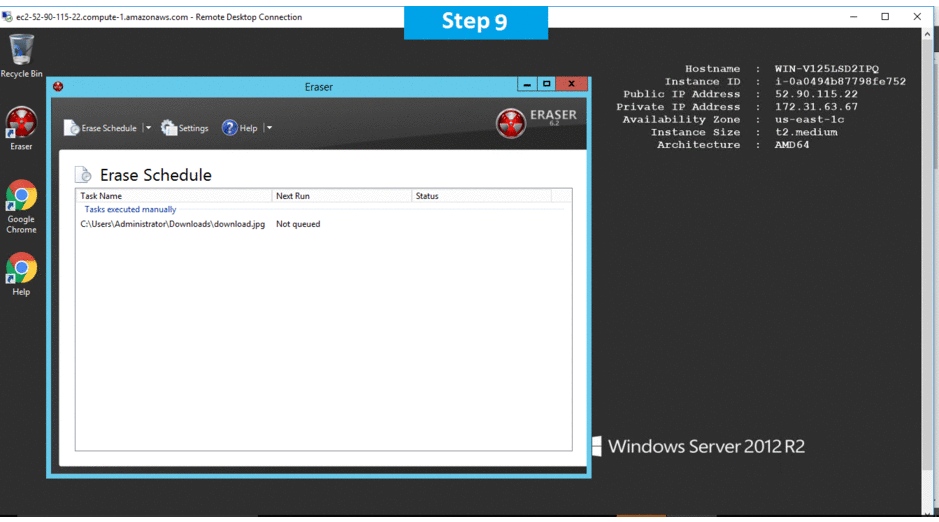
- Selecting Data to Erase
- Creating Recurring Tasks
- Importing/Exporting Tasks
- Running Tasks
- Using the Eraser Command Line
- Creating Custom Erasure Methods
- Erase Browser Caches
- Erase the Recycle Bin
- Erase the Page File and Encrypt the Page File
Major Features of Eraser
-
- Erases residue from deleted files
-
- Erases MFT and MFT-resident files (for NTFS volumes) and Directory Indices (for FAT)
- Powerful and flexible scheduler
AWS
Installation Instructions For Windows
Note: How to find PublicDNS in AWS
Step 1) RDP Connection: To connect to the deployed instance, Please follow Instructions to Connect to Windows instance on AWS Cloud
1) Connect to the virtual machine using following RDP credentials:
- Hostname: PublicDNS / IP of machine
- Port : 3389
Username: To connect to the operating system, use RDP and the username is Administrator.
Password: Please Click here to know how to get password .
Step 2) Click the Windows “Start” button and select “All Programs” and then point to Eraser
Step 3) Other Information:
1.Default installation path: will be in your root folder “C:\Program Files\Eraser”
2.Default ports:
- Windows Machines: RDP Port – 3389
- Http: 80
- Https: 443
Configure custom inbound and outbound rules using this link
Installation Step by Step Screenshots