1-click AWS Deployment 1-click Azure Deployment 1-click Google Deployment
Overview
The Windows File Server role allows customers to share files using attached storage and integrates seamlessly with Active Directory with NTFS permissions. Files are served to end users over SMB file shares that can be mapped as drives or accessed by UNC paths. Mapped drives can be easily deployed to users as they login to their domain joined Windows PC’s through login scripts or group policy rules.
Over time, additional features have been added to Windows File Servers including Previous Versions (Volume Copy Snapshots), Encryption (bit locker), Drive Mirroring and Distributed File System (DFS) that allows administrators to point users to a common name space that is independent of the back-end file server names. More recently Microsoft added Access Based Enumeration (ABE) as an additional way to filter what files and folders users can see based on their NTFS Active Directory permission greatly reducing the need to create separate file server shares for each department or function unit.
.A file server is a server that provides access to files. It acts as a central file storage location that can be accessed by multiple systems. File servers are commonly found in enterprise settings, such as company networks, but they are also used in schools, small organizations, and even home networks.A file server is a central server in a computer network that provides file systems or at least parts of a file system to connected clients. File servers therefore offer users a central storage place for files on internal data media, which is accessible to all authorized clients. Here, the server administrator defines strict rules regarding which users have which access rights: For instance, the configuration or file authorizations of the respective file system enable the admin to set which files can be seen and opened by a certain user or user group, and whether data can only be viewed or also added, edited, or deleted.
A file server may be a dedicated system, such as network attached storage (NAS) device, or it may simply be a computer that hosts shared files. Dedicated file servers are typically used for enterprise applications, since they provide faster data access and offer more storage capacity than non-dedicated systems. In home networks, personal computers are often used as file servers. However, personal NAS devices are also available for home users that require more storage capacity and faster performance than a non-dedicated file server would allow.
File servers can be configured in multiple ways. For example, in a home setting, a file server may be set to automatically allow access to all computers on the local network (LAN). In a business setting where security is important, a file server may require all client systems to log in before accessing the server. Others may only grant access to a specific list of machines, which can be defined by MAC address or IP address. Internet file servers, which provide access to files over the Internet, often require an FTP login before users can download files.
With file servers connected to the internet and configured accordingly, users cannot only access the files via the local network but also benefit from remote access. This enables files to be accessed and saved on the file server even when users are on the go. All modern operating systems such as Windows, Linux, or macOS can be used on a file server, although the devices available in the network need to be compatible with the operating system. But file servers are not only used for file storage and management. They are also often used as a repository for programs that have to be accessible to multiple network participants, and as a backup server.

How do file servers work?
The right hardware is the foundation for a reliable file server. Most importantly, of course, this includes the hard drive which needs to offer sufficient space for the files and necessary programs, as well as the respective operating system, and the software for using the clients. The server also needs enough working memory and processing power to process file and program accesses for various users as quickly and faultlessly as possible. Whether the hardware requirements can be fulfilled by a standard PC or whether a special server setup is required primarily depends on the number of users.
Special network protocols are responsible for communication between file servers and clients: While the SMB protocol (Server Message Block) developed by IBM is used in local networks with Windows and macOS devices, computers with Unix-like systems – such as Linux distributions – largely work with the NFS protocol (Network File System). To combine both protocol types in a single network, clients and file servers based on Unix/Linux must be accordingly equipped with software that implements the SMB protocol in these systems – for example the free software suite Samba.
The functions and options of a file server
As already mentioned, the main functions of a file server are to enable multiple users to access the stored files and free storage space for the file repository. For this reason, these servers are especially popular as a central storage place for internal company files that are not only relevant for individual users. In many cases, companies (particularly in the open-source sector) also use a file server as a download server connected to their own web offering. This way, they allow their customers or website visitors to download select content such as programs, drivers, updates, images, or videos with ease.
The second major application of file servers is data backups. Unlike when saving and jointly managing relevant files, this specifically refers to the creation and maintenance of conventional backups – of system or user files (or both) depending on the need. Storing these backup copies on a file server is both an easy and inexpensive alternative to having to plan and cover the necessary additional storage requirements on each individual client.
What are the advantages of using a file server?
For many companies, using a file server is worth considering for a range of reasons. First, there is of course the advantage of centrality which ensures each authorized network participant can access the stored files. This makes shared working possible on these files. Conflicts between different versions of a document can be practically ruled out, as certain actions – such as editing or deleting – are blocked for other users as soon as you open a file. If users have to share the desired files on their own system instead, or transmit them using removable media, this would be considerably more time-consuming and cumbersome – and it would most likely result in different file versions.
Another key advantage of using file servers is that it relieves the strain on client resources. With the exception of personal documents, essentially all business files and backups can be stored on the file server, depending on how the company wishes to use the file repository. And with the right organization (comprising directories, folders, etc.) users automatically have a much better overview of the entire file inventory.
If the file server is configured for remote access over the internet, the files are also accessible on the go – much like an online storage service. But unlike a cloud solution, the company retains control of the files and their security at all times. This represents a clear advantage over third-party solutions.
File server: Practical but a challenge
The advantages listed clearly show how valuable a file server can be. However, many companies make the mistake of underestimating the work involved in setting up and managing such a server. Companies often do without advance planning. As a result, not only is the hardware stretched to its limits after a short amount of time, but also many of the benefits of a file server don’t take effect. For example, if there is no clear principle for the assignment of rights, situations will likely arise in which users are unable to perform necessary actions. Problems may also occur when the directory and folder structure is unclear – or if no folder structure exists at all.
If you’d like to use a file server, you should therefore consider these aspects from the very beginning, as well as a comprehensive security concept. In the case of the latter, this is important if the file server is also accessible over the internet. The installation and configuration of security software are just as critical as training the employees who access the file server. Only when they have been made aware of topics like cyber security and data protection can the configured protection mechanisms work as intended. This is also true when it comes to storing the files: Clearly communicate where and how files should be saved on the file server to prevent a chaotic data situation from occurring in the first place.
The file server system brought a complete change in implementation of the computer architecture from the mainframe. In this system, the application logic was now executed on the client workstation instead of the server. These servers also provided access to computing resources like printers and large hard drives. The complete File Server Architecture is illustrated in the figure shown below.
The advantage of the file server system is the low cost entry point with flexible arrangement. Computer resources can be added or reduced as and when necessary using this system.
The drawback of the file server architecture is that all application logic is executed on the client machine. The job of the server is to provide files only to store the data. Though the application’s file might be located on the server, the application runs in the client machine’s memory space using the client’s processor. This results in the client machine’s need for large amount of power to run the application.

Taking into account the disadvantages of the centralized system and file server system architectures, the client-server architecture made its advent.
How to Track File and Folder Activities on Windows File Servers:
There are many reasons why you may want to track file and folder activities on Windows File Servers; including data security and compliance. Knowing when users are accessing, reading, creating, modifying or deleting your files and folders is of paramount importance when it comes to ensuring the security and integrity of your File Servers. In this article, we will show you how to keep track of what’s happening to your files and folders using native processes, and also how using LepideAuditor for File Server can help to simplify the entire process. The following are the steps:
Step 1: Configure the “Audit Object Access” audit policy
Perform the following steps to set up this audit policy:
1.On the primary domain controller, or on a workstation where “Administration Tools” are installed, open “Run” dialog box, type “gpmc.msc”, and click “OK” to open the “Group Policy Management” console.
2.In the “Group Policy Management” window, right-click on the default or a customized domain policy, and select “Edit” from the context menu to open the Group Policy Management Editor window.
3.In “Group Policy Management Editor” window, navigate to “Computer Configuration” ➔ “Windows Settings” ➔ “Security Settings” ➔ “Local Policies” ➔ “Audit Policy”.
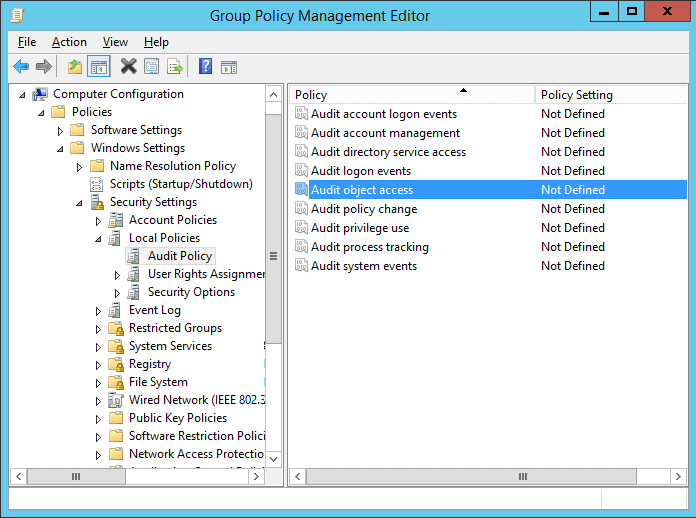
4.Double-click “Audit Object Access” to view its properties.
5.Click “Define these policy settings” checkbox. Click “Success” and “Failure” check boxes
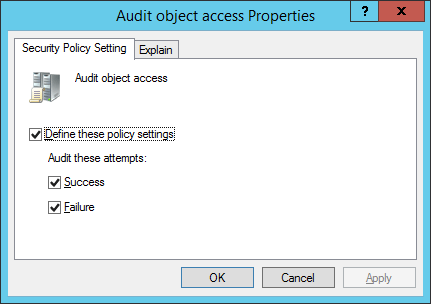
Step 2: Configure auditing on files and folders
Follow the below steps to enable auditing for the files and folders you want to audit on your Windows File Server.
1.Open “Windows Explorer”, and navigate to the folder that you want to track.
2.Right-click the folder and select “Properties” from the context menu. The folder’s properties window appears on the screen.
3.Navigate to “Security” tab
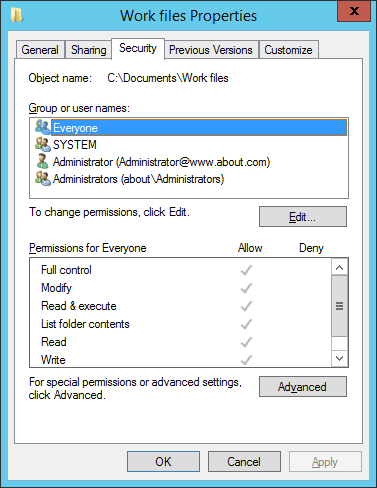
4.Click “Advanced” to access “Advanced Security Settings”. In “Advanced Security Settings” window, navigate to “Auditing” tab.
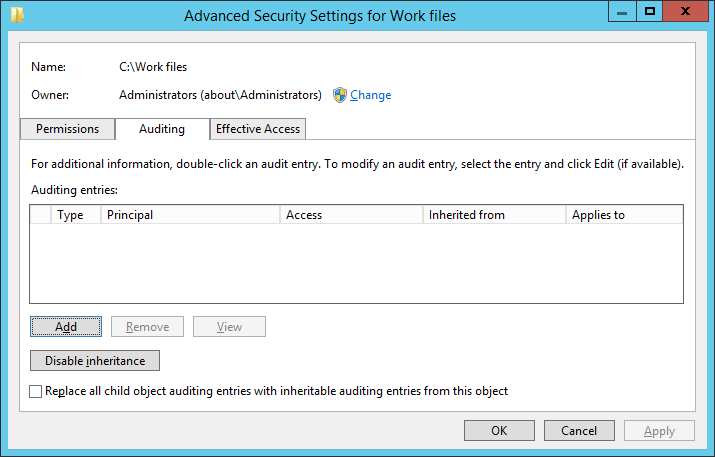
5.To create a new auditing entry, click “Add”. “Auditing Entry” window appears on the screen.
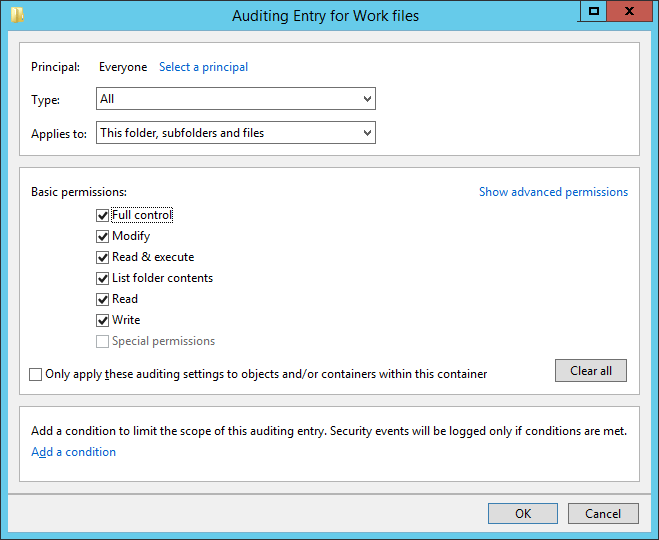
6.Click “Select a Principal” to choose users whose activities you want to track.
7.“Select User, Computer, Service Account, or Group” dialog box appears on the screen. If you want to audit all users’ activities, enter “Everyone” in the “Enter the object name to select” dialog box, and click “Checknames”. In our case, we enter “Everyone”.
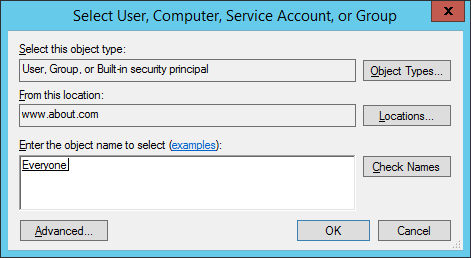
8.Click “OK” to finalize your selection. It takes you back to “Auditing Entry” window.
9.Select “All” in “Type” drop-down menu to monitor both successful and failure events. You can select “Success” to monitor only successful events or you can select “Failure” to monitor only failure events.
10.In “Applies to” drop-down menu, select “This folder, subfolder, and files” option, if you want to audit all the subfolders and the files within this folder.
11.Click “Show advanced permission” option in the permissions section to view all the permissions. Select all the actions that you want to audit. If you want to audit all the actions, click “Full Control” checkbox. Here, we have selected “Full Control” checkbox.
12.Click “OK” to apply the auditing settings. It closes “Auditing Entry” window.
13.Now on “Auditing” tab of “Advanced security settings” window, you can see the newly added audit entry.
14.Click “Apply” and “OK” in the “Advanced Security Setting” window to close it.
15.Click “Apply” and “OK” to close the folder properties window.
Step 3: View Events in Windows Event Viewer
After you have configured the above audit settings, you can track any change made to folders, subfolders and files. For that, open “Windows Event Viewer” and go to “Windows Logs” ➔ “Security”. In the right pane, use the “Filter Current Log” option to find the relevant events.
For example, if anyone creates a new file, event ID 4656 and Event ID 4663 will both be logged. To illustrate this, in our case, a file has been created in the “Work files” folder. In the following image, you can see the details of the event ID 4656:
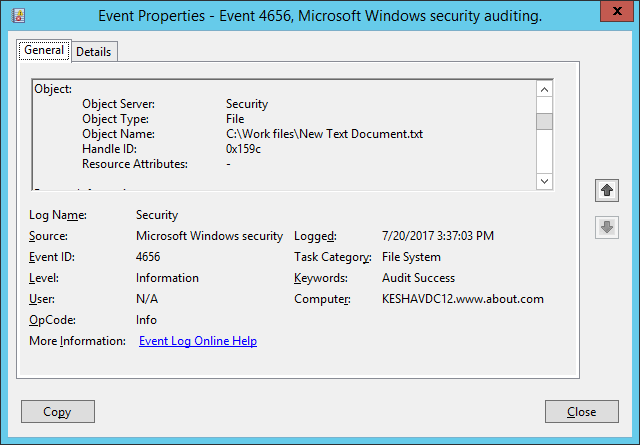
You can see the new file’s name (C:\Work files\New Text Document) which is visible after you scroll down the side bar.The same event ID 4656 shows all accesses made to the objects, such as files and folders.
Windows File Server, codenamed “Windows Server 8”,is the sixth release of Windows Server. It is the server version of Windows 8 and succeeds Windows Server 2008 R2. Two pre-release versions, a developer preview and a beta version, were released during development. The software was generally available to customers starting on September 4, 2012.
Unlike its predecessor, Windows Server 2012 has no support for Itanium-based computers, and has four editions. Various features were added or improved over Windows Server 2008 R2 (with many placing an emphasis on cloud computing), such as an updated version of Hyper-V, an IP address management role, a new version of Windows Task Manager, and ReFS, a new file system. Windows Server 2012 received generally good reviews in spite of having included the same controversial Metro-based user interface seen in Windows 8.
Cognosys Provides Hardened images of Windows File Server on the cloud ( AWS marketplace, Azure and Google Cloud Platform).
Deploy Windows File Server securely on cloud i.e. AWS marketplace, Azure and Google Cloud Platform (GCP)
The successor to Windows Server 2012, called Windows Server 2012 R2, was released along with Windows 8.1 in October 2013. A service pack, formally designated Windows Server 2012 R2 Update, was released in April 2014.
Features
General features of Windows file server:
Storage
Regardless of the location of files server shares, storage is a critical component of any Windows File Server role. Since storage will be accessed by multiple users simultaneously speed and redundancy are of critical importance. Windows File Server supports mirroring disks into a redundant array of independent disks (RAID) to ensure a failure of any one disk will still allow the File Server to available to users. Server disks are typically designed to handle the stress of being in operation 24×7 and have a longer lifetime than regular desktop hard drives. Solid State Drives can also be used to improve performance and redundancy since there are no moving parts.
Security
Windows File Server integrated seamlessly with NTFS and active directory. Windows File Sharing is easy to deploy to 1000’s of user’s based on active directory group membership. In addition to allowing users access to shares by group, administrators can also use global deny, share level and Access Based Enumeration to further limit user File Server share permissions. Files may also be encrypted when stored on disk.
Remote Access
As more users began working remotely with the development of the internet remote access to Windows File Servers became necessary. In the initial stages user’s may have used insecure VPN protocols like PPTP that was built into Windows File Server and Client PC’s. This was inefficient since each user would need to be manually provisioned and PPTP and NetBios was not designed to withstand the security needed over the internet. Over time new VPN options have been made available over IPsec, however these also allow direct network access, have not always easily provisioned and are now subject to security concerns such as ransomware.
Many smaller companies are now storing their files in public sync and share vendors with the ability to connect to files over a web browser, desktop sync or mobile client. For larger firms the prospect of migrating many years and terabytes or even petabytes of data is not feasible. These firms may also have data compliance or sovereignty issues to consider. Using traditional VPN is also expensive to maintain, support and increasingly a security concern.
Major Features of Windows File Server 2012
1. New Server Manager: Create, Manage Server Groups
One of the benefits of the newServer Manager interface is the capability to create server groups, which are collections of servers that already exist on your network and can be managed through the new user experience. Creating new server groups lets you manage tasks among each server with common attributes—a server group containing all machines running IIS, for example, a group of all database servers, and so on—and provide specific information on any of them as you wish. This is a big boon for organizations without dedicated monitoring software in place.
2. Better Edition, SKU Selection
Kudos to Microsoft for cleaning up what was a muddy value proposition. The core OS is now the same, and the edition you buy—Standard or Datacenter—depends on whether you want to run up to two virtual machines as guests or if you’d like unlimited guest virtualization. There’s no Enterprise edition gumming up the works. This is a big win for everyone.
3. A Command-Line First, GUI-Second Mentality
The emphasis for Windows Server has changed from a GUI-first philosophy to a GUI-optional mindset. Indeed, when you first install the OS, youre asked to choose between a core and a full installation. Core is the preferred, and encouraged, option. Once you install a core version of Windows Server 2012, you can flip on a GUI simply by installing the GUI role, and you can then opt to take it off without a full reinstall.
This is a great feature when you first deploy a server. You can use the GUI to take care of all of the mundane configuration tasks, but when the machine is ready for production, you can flip the GUI off and deploy. This offers a number of benefits, including reducing the attack surface, resource load and energy requirements.
4. Hyper-V Replication
The Hyper-V Replica feature allows you to replicate a virtual machine from one location to another with Hyper-V and a network connection—and without any shared storage required. This is a big deal in the Microsoft world for disaster recovery, high availability and more. VMware does this, too, but the vendor charges new licensees extra for the capability.
5. Expanded PowerShell Capabilities
There are hundreds more cmdlets in the latest version of Windows Server. This will make your life easier, since PowerShell is essentially the preferred method of managing all of the workloads you can run on the operating system.
6. Storage Spaces: Flipping Complexity on Its Head
Storage Spaces is an innovative features that basically takes commodity storage hardware—inexpensive drives and their controllers, like a JBOD (informal parlance for Just a Bunch of Disks—and turns it into a pool of storage that is divided into spaces that are in turn used just like regular disks.
7. DirectAccess: A VPN Without the Pain of a VPN
DirectAccess allows VPN-like secure tunneling from any endpoint back to the corporate network without the overhead and performance hit of a true VPN. There is also no management agent on the client. When the technology is configured correctly, it just works—users have seamless connectivity to file shares, on-premises equipment and other resources just as if they were on the corporate campus. In addition, group policy objects get applied and administrators can manage machines wherever they are, not just when they come to headquarters or when they connect up to the VPN. This technology had previously been difficult to set up, but in Windows Server 2012, it very much just works.
8. Dynamic Access Control: New Way of Thinking
Dynamic Access Control (DAC) is a suite of facilities that really enhances the way you can control access to information. It’s no longer about taking files or folders and making decisions about “Yes, these people can” and “No, these people can’t.”
9. Resilient File System: An Evolution of NTFS
The Resilient File System (ReFS) was designed as an evolution of the New Technology File System (NTFS) with a focus on availability and integrity. ReFS writes to different locations on disk in an atomic fashion, which improves data resiliency in the event of a power failure during a write, and includes the new “integrity streams” feature that uses checksums and real-time allocations to protect the sequencing and access of both system and user data.
10. Out-of-the-Box IP Address Management
In the box with Windows Server 2012, youll find a complete IPAM suite. This is something many medium-sized businesses simply don’t have access to. With the IPAM suite, you can allocate, group, issue, lease and renew IP addresses in an organized fashion, as well as integrate with the in-box DHCP and DNS servers to discover and manage devices already on your network.
AWS
Installation Instructions for Windows
Note: How to find PublicDNS in AWS
Step 1) RDP Connection: To connect to the deployed instance, Please follow Instructions to Connect to Windows instance on AWS Cloud
1) Connect to the virtual machine using following RDP credentials:
- Hostname: PublicDNS / IP of machine
- Port : 3389
Username: To connect to the operating system, use RDP and the username is Administrator.
Password: Please Click here to know how to get password .
Step 2) Choose Start, expand All Programs, and then expand Windows File Server 2012
Step 3) Other Information:
Default ports:
- Windows Machines: RDP Port – 3389
- Http: 80
- Https: 443
Configure custom inbound and outbound rules using this link
Azure
Installation Instructions for Windows
Note: How to find PublicDNS in Azure
Step 1) RDP Connection: To connect to the deployed instance, Please follow Instructions to Connect to Windows instance on Azure Cloud
Connect to virtual machine using following RDP credentials:
- Hostname: PublicDNS / IP of machine
- Port : 3389
Username: Your chosen username when you created the machine ( For example: Azureuser)
Password : Your Chosen Password when you created the machine ( How to reset the password if you do not remember)
Step 2) Click the Windows “Start” button and select “All Programs” and then point to Windows File Server 2012
Step 3) Other Information:
Default ports:
- Windows Machines: RDP Port – 3389
- Http: 80
- Https: 443
Configure custom inbound and outbound rules using this link
Azure Step By Step Screenshots
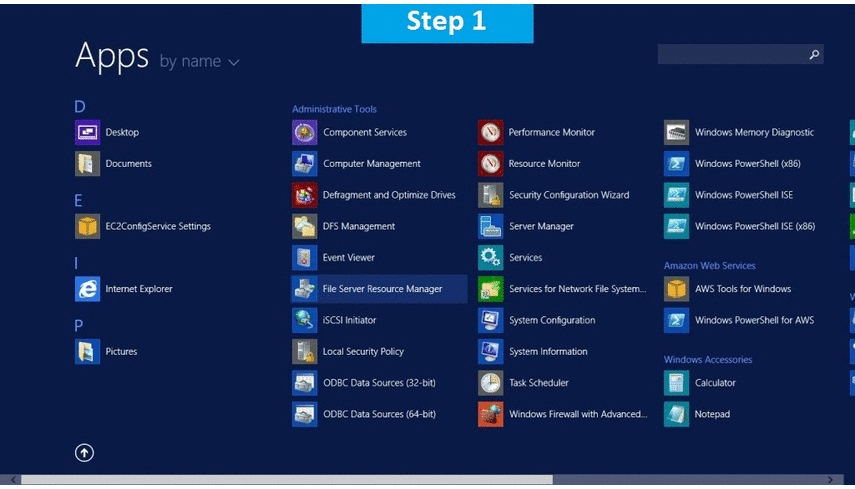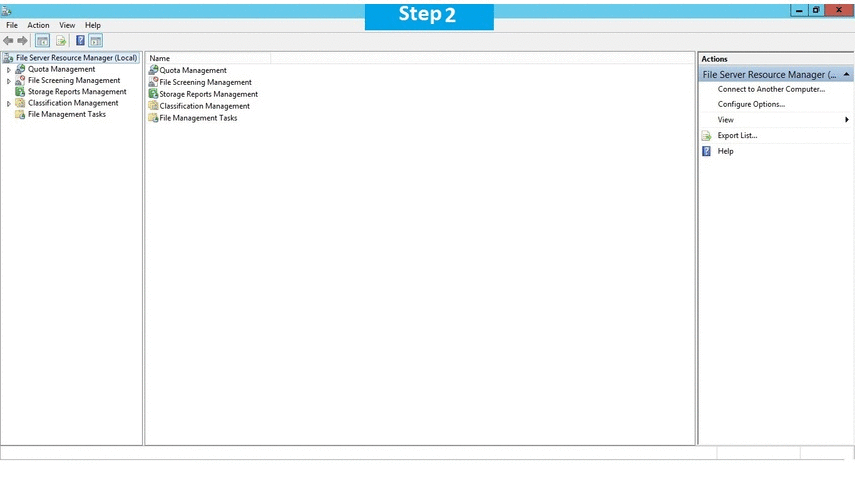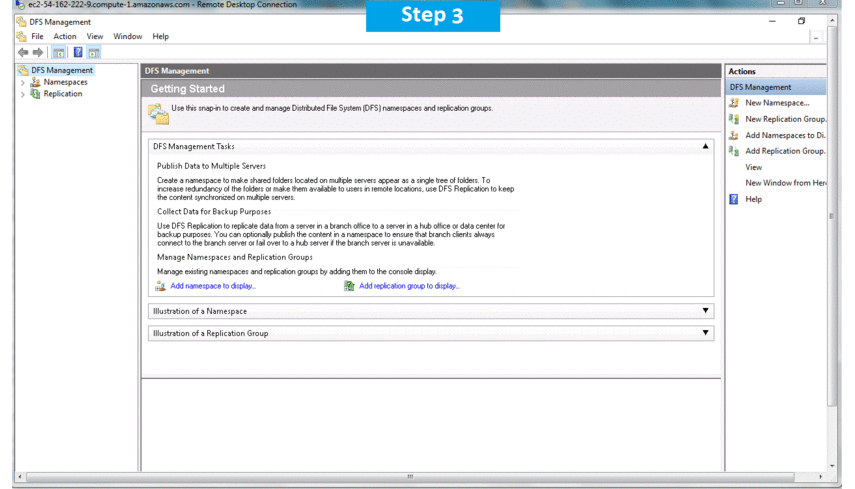
Installation Instructions For Windows
Step 1) VM Creation:
1.Click the Launch on Compute Engine button to choose the hardware and network settings.
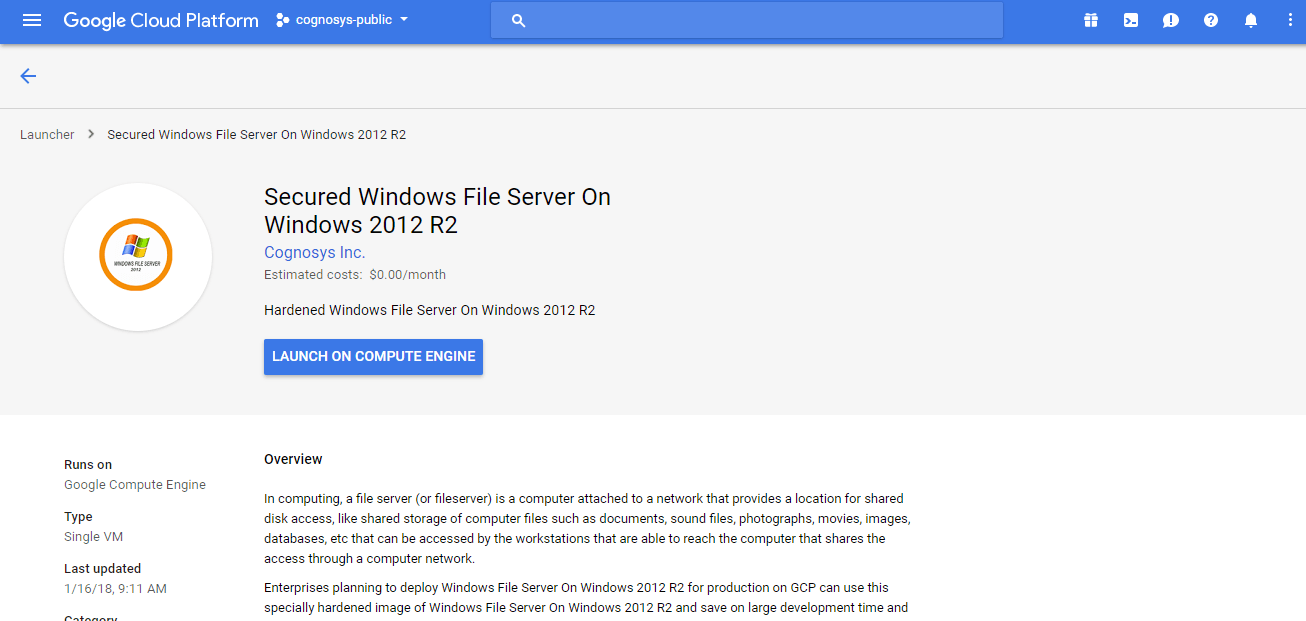
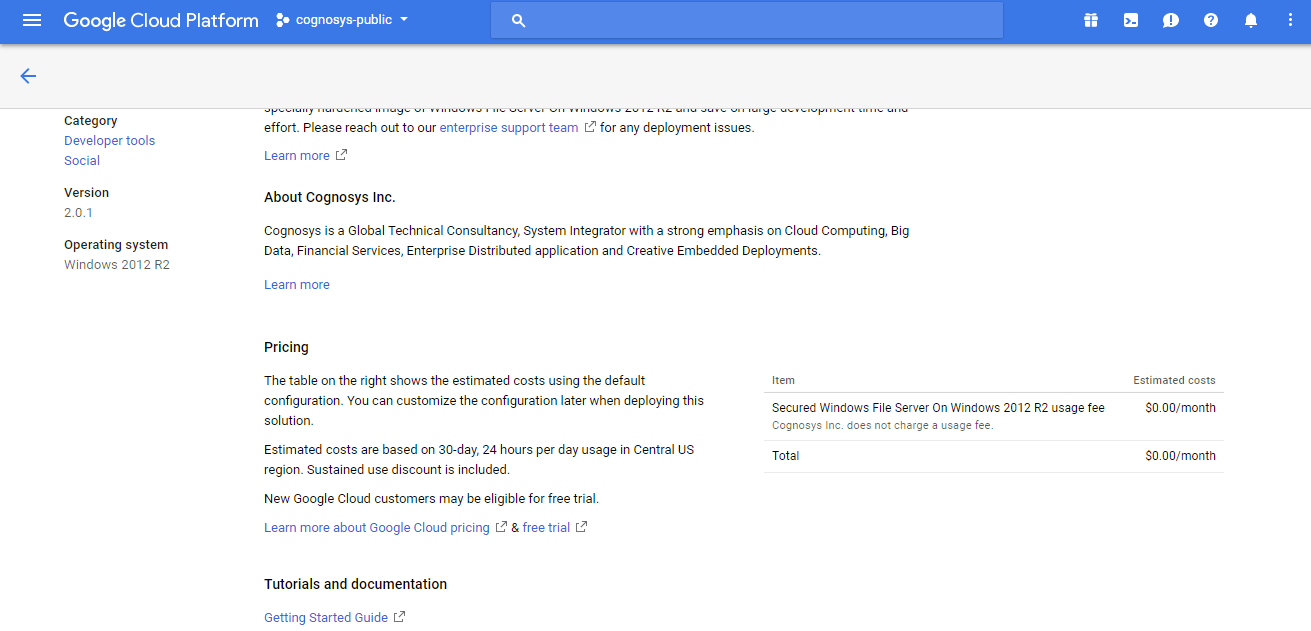
2.You can see at this page, an overview of Cognosys Image as well as some estimated costs of VM.
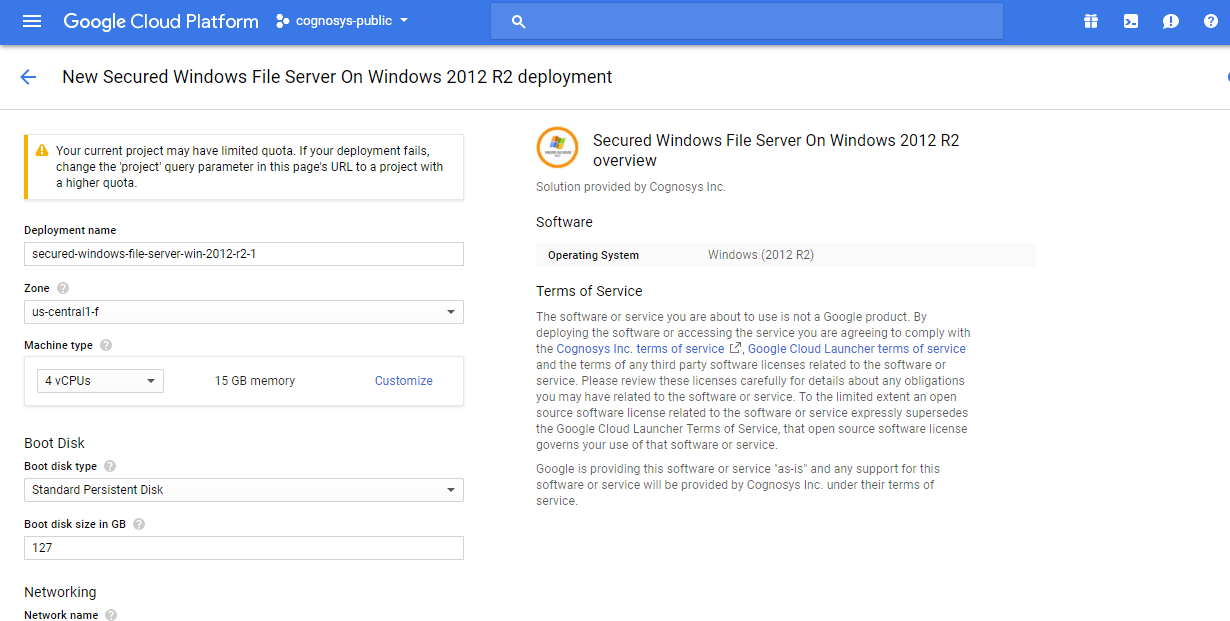
3.In the settings page, you can choose the number of CPUs and amount of RAM, the disk size and type etc.
Step 2) RDP Connection: To initialize the DB Server connect to the deployed instance, Please follow Instructions to Connect to Windows instance on Google Cloud
Step 3) Choose Start, expand All Programs, and then expand Windows File Server 2012
Step 4) Other Information:
Default ports:
- Windows Machines: RDP Port – 3389
- Http: 80
- Https: 443
Videos
Windows Server 2012 R2, Installation, Migration, and Getting Started, Module 3
How to Install Windows Server 2008 R2