1-click AWS Deployment 1-click Azure Deployment
Overview
Mobile device management is an industry term for the administration of mobile devices, such as smartphones, tablet computers and laptops. MDM is usually implemented with the use of a third-party product that has management features for particular vendors of mobile devices. Mobile device management (MDM) is software that allows IT administrators to control, secure and enforce policies on smartphones, tablets and other endpoints.
MDM is a core component of enterprise mobility management (EMM), which also includes mobile application management, identity and access management, and enterprise file sync and share. The intent of MDM is to optimize the functionality and security of mobile devices within the enterprise while simultaneously protecting the corporate network.
Modern enterprise mobility products support not only smartphones but also tablets, Windows 10 and macOS computers and even some internet of things (IoT) devices. The practice of using MDM to control PCs is known as unified endpoint management (UEM). UEM is widely considered the successor to MDM and aims to manage all enterprise devices with a single console.
In just a few short years, the way mobile devices are used by employees has shifted dramatically. Increasingly, employees are bringing their own devices to their workplaces and connecting to secure corporate networks. While employees enjoy the flexibility and ease this offers, employers also appreciate the added benefits of increased efficiency with lower equipment costs.
However, with this trend comes a set of new considerations for security, connectivity, privacy and management. Employees also have varied mobile service providers, and their devices run varied operating systems. The inherent risks of a “bring your own device” (BYOD) policy has given rise to mobile device management (MDM) software used by an IT department to monitor, manage, and secure employees’ laptops, smartphones, tablets, and other devices that are being used in the workplace. With security and data breaches becoming costlier every year, MDM tools have become essential to the modern workplace
Coupled with additional tools, technologies, processes, and policies, an MDM solution is a core component of enterprise mobility management (EMM), an ever-developing organizational trend that addresses the business and technological context of device usage in everyday business operations. However, not all MDM tools are created equal, and the right choice for SMBs may depend on a variety of factors.
The Evolution of Mobile Device Management (and EMM)
The field of mobile device management has continued to evolve as more professionals are using laptops and smartphones to work. This has increased the need for solutions that allow employees to access information wherever they are and at any time. Early solutions focused solely on devices, and lacked application and content management; today, they are now growing into broader EMM solutions to better capture and serve the mobile opportunity.
Current EMM suites consist of policy- and configuration-management tools that are coupled with a management overlay for applications and content that’s intended for mobile devices, which are smartphone-OS specific. IT organizations and service providers use EMM suites to deliver IT support to mobile end users and to maintain security policies.
Modern EMM suites provide the following core functions:
- Hardware inventory
- Application inventory
- OS configuration management
- Mobile app deployment, updating and removal
- Mobile app configuration and policy management
- Remote view and control for troubleshooting
- Execute remote actions, such as remote wipe
- Mobile content management
Key Terms & Definitions
Bring your own device (BYOD) is a term referring to a trend where employees are bringing or connecting their own computing devices to the workplace for use and connectivity on the secure corporate network.
Content Access: A connection to a back-end repository where users can pull content to their devices. Specific capabilities include support for specific back-end repositories (SharePoint, Documentum, etc.), roaming download restrictions, and audit logging to track who accesses/downloads files.
Enterprise mobility management (EMM) is the collective set of tools, technologies, processes, and policies used to manage and maintain the use of mobile devices within an organization. EMM is an evolving organizational trend that deals with the business as well as technological context of the increasing trend of mobile and handheld device usage in routine business operations. MDM software is often combined with additional security services and tools to create a complete mobile device and security EMM solution.
Mobile application management applies management and policy control functionality to individual applications, which are then managed by the EMM console. This capability is necessary when a device’s operating system (e.g., iOS, Android, Windows Phone) does not provide the required management capability or when organizations elect not to install an MDM profile on the device. There are two basic forms of mobile application management:
- Preconfigured applications: These generally include a secure personal information manager (PIM) for email, calendars, and contact management, as well as a secure browser provided by the EMM provider or a third party. These tools are configured to be managed and secured by the EMM system.
- Application extensions:These apply policies to applications through the use of a software development kit (SDK) or by wrapping. This capability is necessary when the OS does not provide the required management capability or when organizations elect not to install an MDM agent on the device.
Mobile content management enables users to access content from their mobile devices. The mobile content management function within EMM suites has three fundamental roles:
- Secure Container: A client-side app that enables a user to store content securely on a mobile device. The EMM can enforce policies such as authentication, file sharing and copy/paste restriction. Content comes from three primary sources: email (and attachments), content pushed by the administrator or another internal person, and content accessed from a back-end repository
- Content Push: Push-based document delivery. Some specific functions are to control document versions, to alert users of new files, and to flag a content expiration date
Mobile device management (MDM) is a type of security software used by an IT department to monitor, manage, and secure employees’ mobile devices (laptops, smartphones, tablets, etc.) that are deployed across multiple mobile service providers and across multiple mobile operating systems being used in the organization. MDM is a great way to expand the capabilities of traditional RMM.
Remote monitoring and management (RMM) is a type of software designed to help managed IT service providers remotely and proactively monitor client endpoints, networks and computers. This is also now known as or referred to as remote IT management.
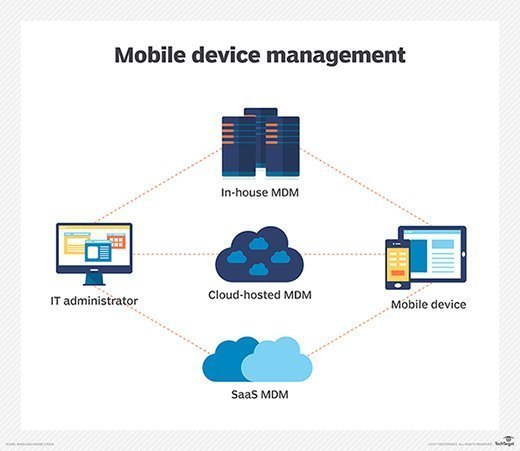
How mobile device management works :
Mobile device management relies on endpoint software called an MDM agent and an MDM server that lives in a data center, either on premises or in the cloud.
IT administrators configure policies through the MDM server’s management console, and the server then pushes those policies over the air to the MDM agent on the device. The agent applies the policies to the device by communicating with application programming interfaces (APIs) built directly into the device operating system.
Similarly, IT administrators can deploy applications to managed devices through the MDM server.
Why Businesses Need MDM
The rapid adoption of smartphones and tablets, along with increasing numbers of employees who are working from home or other non-traditional locations, has placed mobility solutions near the top of many business’ priority lists.
A recent study by Gartner indicates that PC sales are in decline – the majority (87%) of devices shipping in 2015 will be mobile phones and tablets. As a result, 451 Research predicts that the $3.8 billion EMM (enterprise mobile management) market will double to $9.8 billion by 2018. SMBs have been adopting mobile solutions at a fast and furious pace. SMB Group research indicates that 67% of SMBs now view mobile solutions and services as “critical” to their businesses, and 83% have already deployed mobile apps to help improve employee productivity. Of these, 55% are using mobile apps for specific business functions, such as CRM or order entry, and 49% of SMBs are building mobile-friendly websites, and/or deploying mobile apps to engage and transact with customers.
EMM is clearly trending, and looks to continue to do so in the future. After looking at the risks of doing business without a proper MDM solution, it becomes obvious why. Without MDM, information on stolen or lost devices is not secure, which could allow it to easily fall into the wrong hands. Also, devices without MDM have an increased exposure to malware and other viruses that could compromise confidential data. And, once that confidential data is compromised, the ease of which a data breach or hacking incident can be achieved increases greatly – events that can permanently affect a company’s reputation with consumers and other business partners. According to Novell, a laptop or tablet is stolen every 53 seconds, and 113 cell phones are lost or stolen every minute. With the cost to recover from a corporate data breach getting increasingly more expensive every year, more and more businesses are seeing the value of a comprehensive EMM solution.
What to Look for in an MDM Solution
Once resolved to pursue an MDM solution, one will find that there are multiples options available in the market. While many features will vary, certain criteria that are essential:
- Cloud-based, so updates are automatic and painless
- Fully managed, 24/7 monitoring
- Remote configuration and monitoring
- Passwords, blacklists and other security policies enforcement
- Passcode enforcement/remote data wiping, to preventunauthorized access to the phone
- Geofencing, to restrict access to specific data andapplications based on location
- Backup/restore functionality of corporate data
- Logging/reporting for compliance purposes
- Jailbreaking and rooting alerts for users attempting to bypass restrictions
- Remote disconnection or disabling of unauthorized devices and applications
- Scalable, so new users and increasingly sophisticated devices can be accommodated easily
MDM solutions, however, are only as useful as their implementation; they will only succeed if they are executed properly. Care and due diligence must be taken to evaluate an MDM platform to understand if it fits a company’s specific policies.
Set up Mobile Device Management :
Step 1: (Required) Configure domains for MDM
If you don’t have a custom domain associated with Office 365 or if you’re not managing Windows devices, you can skip this section. Otherwise, you’ll need to add DNS records for the domain at your DNS host. If you’ve added the records already, as part of setting up your domain with Office 365, you’re all set. After you add the records, Office 365 users in your organization who sign in on their Windows device with an email address that uses your custom domain are redirected to enroll in Mobile Device Management for Microsoft 365 Business Standard.
After you add the two records, go back to the Security & Compliance Center and navigate to Device management > Manage settings to complete the next step.
Step 2: (Required) Configure an APNs Certificate for iOS devices
To manage iOS devices like iPad and iPhones, you need to create an APNs certificate.
- Sign in to Office 365 with your global admin account.
- In your browser type: https://protection.office.com.
- Select Data loss prevention > Device management, and choose APNs Certificate for iOS devices.
- On the Apple Push Notification Certificate Settings page, choose Next.
- Select Download your CSR file and save the Certificate signing request to a somewhere on your computer that you’ll remember. Select Next.
- On the Create an APNs certificate page:
- Select Apple APNS Portal to open the Apple Push Certificates Portal.
- Sign in with an Apple ID.
- Select Create a Certificate and accept the Terms of Use.
- Browse to the Certificate signing request you downloaded to your computer from Office 365 and select Upload.
- Download the APN certificate created by the Apple Push Certificate Portal to your computer.
7.Go back to Office 365 and select Next to get to the Upload APNS certificate page.
8.Browse to the APN certificate you downloaded from the Apple Push Certificates Portal.
9.Select Finish.
After you add APN Certificate, go back and navigate to Manage organization-wide device access settings to complete the next step.
Step 3: (Recommended) Set up multi-factor authentication
If you don’t see multi-factor authentication (MFA) under Recommended steps, you can skip this section. If this option is listed, we recommend you turn on MFA in the Azure AD portal to increase the security of the Mobile Device Management for Microsoft 365 Business Standard enrollment process. It is turned off by default.
MFA helps secure the sign in to Office 365 for mobile device enrollment by requiring a second form of authentication. Users are required to acknowledge a phone call, text message, or app notification on their mobile device after correctly entering their work account password. They can only enroll their device after this second form of authentication is completed. After users’ devices are enrolled in Mobile Device Management for Microsoft 365 Business Standard, users can access Office 365 resources with just their work account.
Next to Set up multi-factor authentication, select Set up. To learn how to turn on MFA in the Azure AD portal, see Set up multi-factor authentication.
After you set up MFA, go back to the Security & Compliance Center and navigate to Device management > Manage settings to complete the next step.
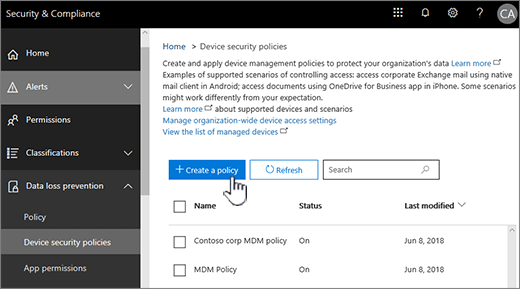
Step 4: (Recommended) Manage device security policies
The next step is to create and deploy device security policies to help protect your Office 365 organization’s data. For example, you can help prevent data loss if a user loses their device by creating a policy to lock devices after 5 minutes of inactivity and have devices wiped after 3 sign-in failures.
- Sign in to Office 365 with your global admin account.
- Click this link: Activate Mobile Device Management. If the service is Activated you will see a link to the Manage Devices instead the activation steps.
- Go to Device policies and select Manage organization-wide device access settings.
Pros and Cons of Mobile Device Management :
With the evolving technology, mobile devices have gained prominence over stationary ones. People use Laptops 79% Smartphones 87% Tablets 68% Why MDM? MDM solution is essential if the companies are hoping for a flexible working environment, along with appropriate level of security.
Pros of MDM:
Manage Devices and Users Remotely 2.Device Update 3.Controls Application Download 4.Automatic Device Registration 5.Data Backup 6.Security Policy Enforcement 7.Favors BYOD
Manage Devices and Users Remotely Controlling mobile devices remotely enables you to disable unauthorized users or applications.
Device Update To protect your security and data, MDM allows centralized control and audit of the updates.
Controls Application Download MDM allows download of applications and provides centralized control to allow users to install these applications.
Automatic Device Registration MDM solutions can register new devices automatically.
Data Backup Failure of any mobile device does not result in loss of information. Security Policy Enforcement MDM ensures that there is no security breach by implementing access limitations and password protection.
Favors BYOD With BYOD the company can save costs and increase productivity. But BYOD doesn’t mean completely compromising with security while using personal device
Cons of MDM :
Security Gaps
Regular Security Audits Required
Cloud Services
Costly
Security Gaps MDM requires trained IT staff and administrator and certain policies to monitor use of an organizations data and policies.
Regular Security Audits Required MDM does provide security but that doesn’t mean the company should completely rely on it.
Cloud Services MDM can’t prevent data leakage through cloud services.
Costly Some companies may already have invested in desktop computers or laptops which can prevent them from adopting MDM.
-Mobile device management (MDM) is a type of security software used by an IT department to monitor, manage and secure employees’ mobile devices that are deployed across multiple mobile service providers and across multiple mobile operating systems being used in the organization.
Mobile device management software is often combined with additional security services and tools such as Mobile Application Management to create a complete mobile device and security Enterprise Mobility Management solution.
Mobile Device Management on cloud For AWS
Features
Mobile device management features :
The developers of mobile operating systems and manufacturers of mobile devices control what MDM software can and can’t do on their devices through their APIs. As a result, mobile device management has become a commodity, with most vendors offering a similar set of core capabilities. MDM vendor differentiation comes by integrating mobile device management servers with other enterprise software.
Common mobile device management features include:
- device inventory and tracking;
- app distribution and/or an enterprise app store;
- remote wipe;
- password enforcement;
- app whitelisting and blacklisting; and
- data encryption enforcement.
Major Features of Mobile Device Management :
1.Device enrollment:
Enroll devices over-the-Air (OTA), with Microsoft’s built-in device management client.
Enable users to help themselves with a self-service portal.
Authenticate enrollment with a one-time passcode or the user’s Active Directory credential.
Enroll multiple devices for a single user.
2.Profile management
Create and configure your email settings policy for IMAP, POP and Exchange.
Configure your WiFi, VPN and cellular data use while roaming.
Customize the security level of passcodes ranging from simple to complex depending on the need.
Segregate windows phones based on corporate or BYOD and apply policies and restrictions as needed.
Provide email access to only MDM enrolled devices with Exchange ActiveSync.
3.App management
Securely manage and distribute in-house apps.
Distribute the apps in the App Catalog to users
Silently deploy apps without user intervention.
Segregate blacklisted and whitelisted of apps.
Delete distributed apps automatically with actions such as “remove device” or “corporate wipe”.
Gather reports to monitor the status of installed apps in all devices.
4.Security management
Remote lock your devices to protect your data in the occurence of a lost or stolen device.
Configure security settings such as restricting copy and paste operations, location services, camera, and NFC.
Activate a remote alarm to identify a lost device.
Perform clean wipe to prevent data loss or theft.
Execute a corporate wipe to erase products distributed via Windows Phone Management.
5.Audit & Reports
Monitor the status of your Windows Phones by generating updated reports.
Generate customized reports based on criteria such as applications by devices, devices by model, and more.
AWS
Installation Instructions For Windows
Note: How to find PublicDNS in AWS
Step 1) RDP Connection: To connect to the deployed instance, Please follow Instructions to Connect to Windows instance on AWS Cloud
1) Connect to the virtual machine using following RDP credentials:
- Hostname: PublicDNS / IP of machine
- Port : 3389
Username: To connect to the operating system, use RDP and the username is Administrator.
Password: Please Click here to know how to get password .
Step 2) Click the Windows “Start” button and select “All Programs” and then point to Mobile Device Management .
Step 3) Other Information:
1. Default installation path: will be in your root folder “C:\ManageEngine\MDMServer”
2. Default ports:
- Windows Machines: RDP Port – 3389
- Http: 80
- Https: 443
Note:
1.Click on Desktop icon – Press start, then App will open in browser.
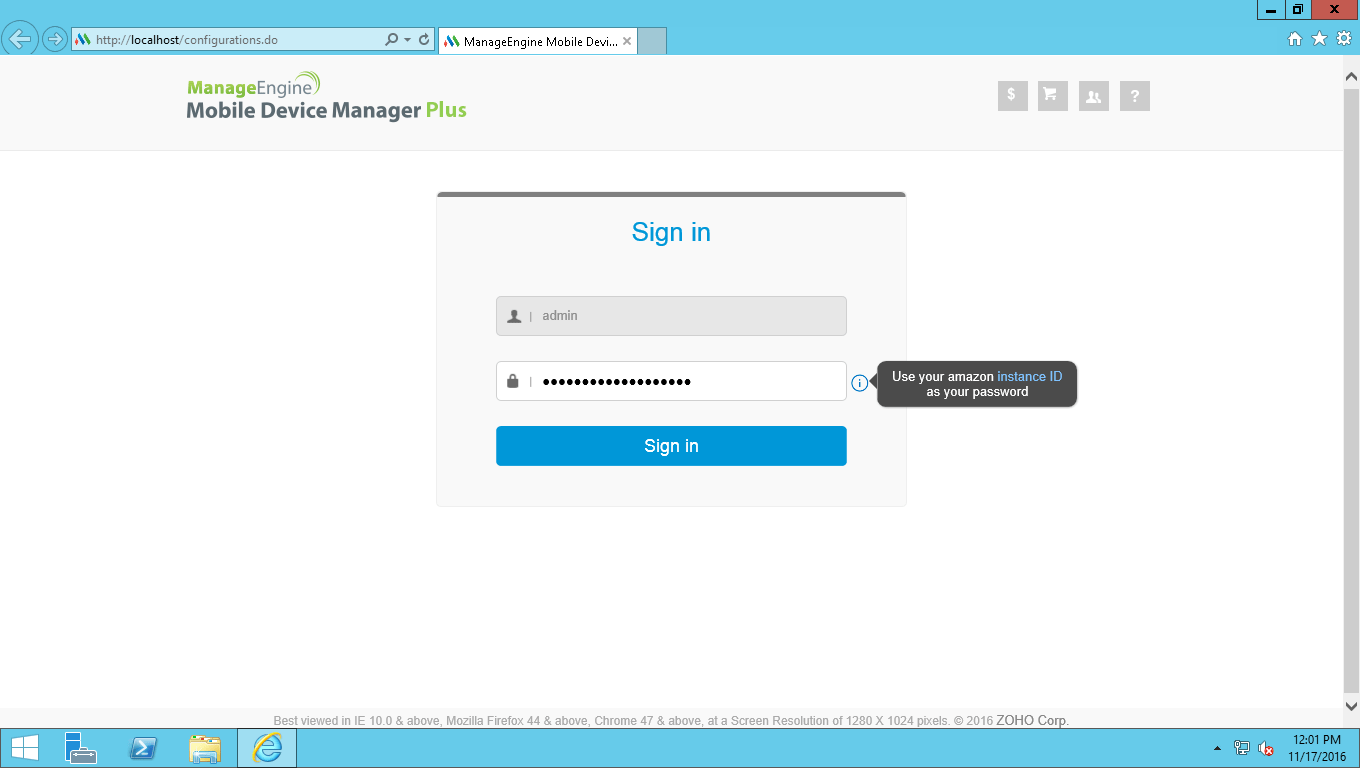
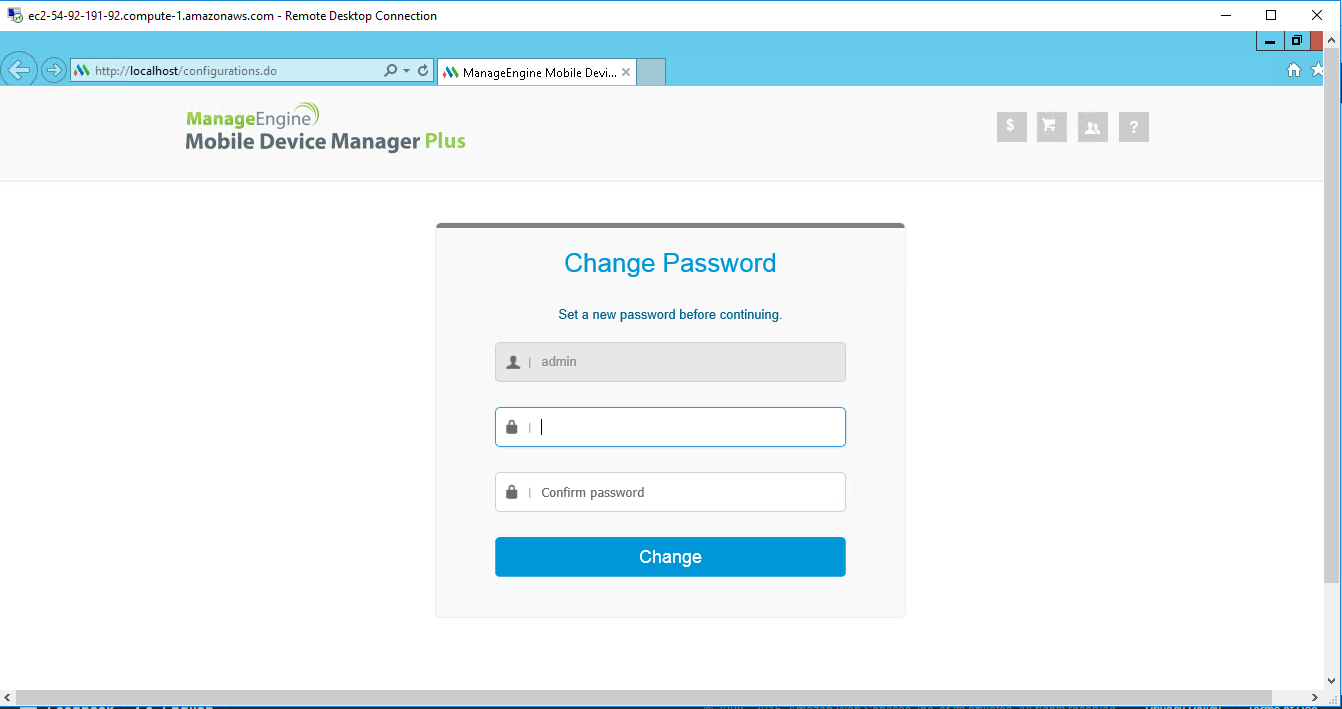
2.Open Browser and type URL – ‘http://localhost/’ to open application .
3.Your Amazon Instance ID is your Password.
Configure custom inbound and outbound rules using this link
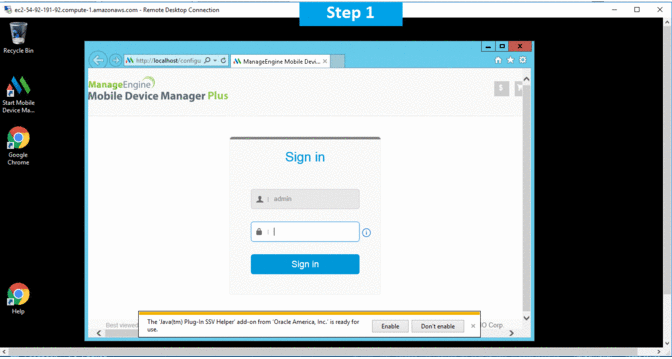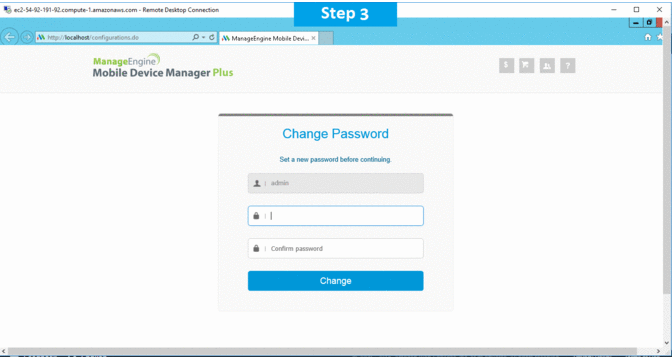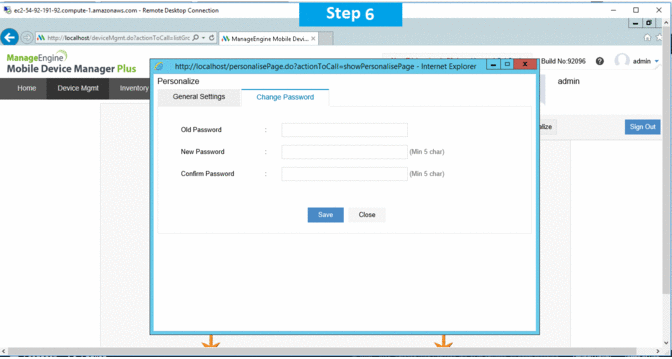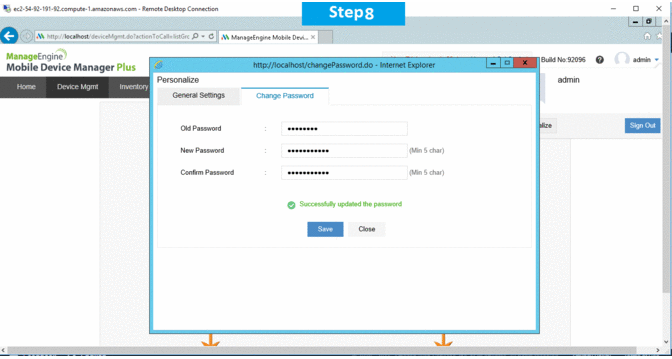
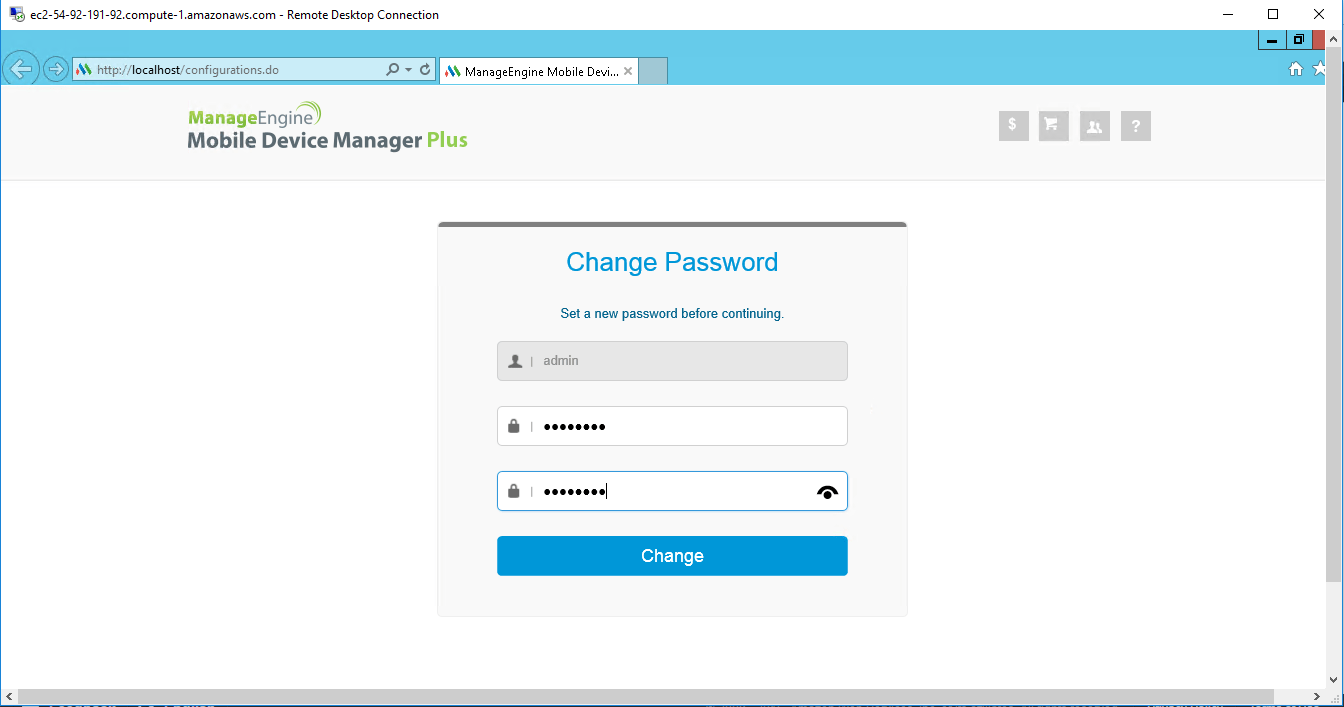
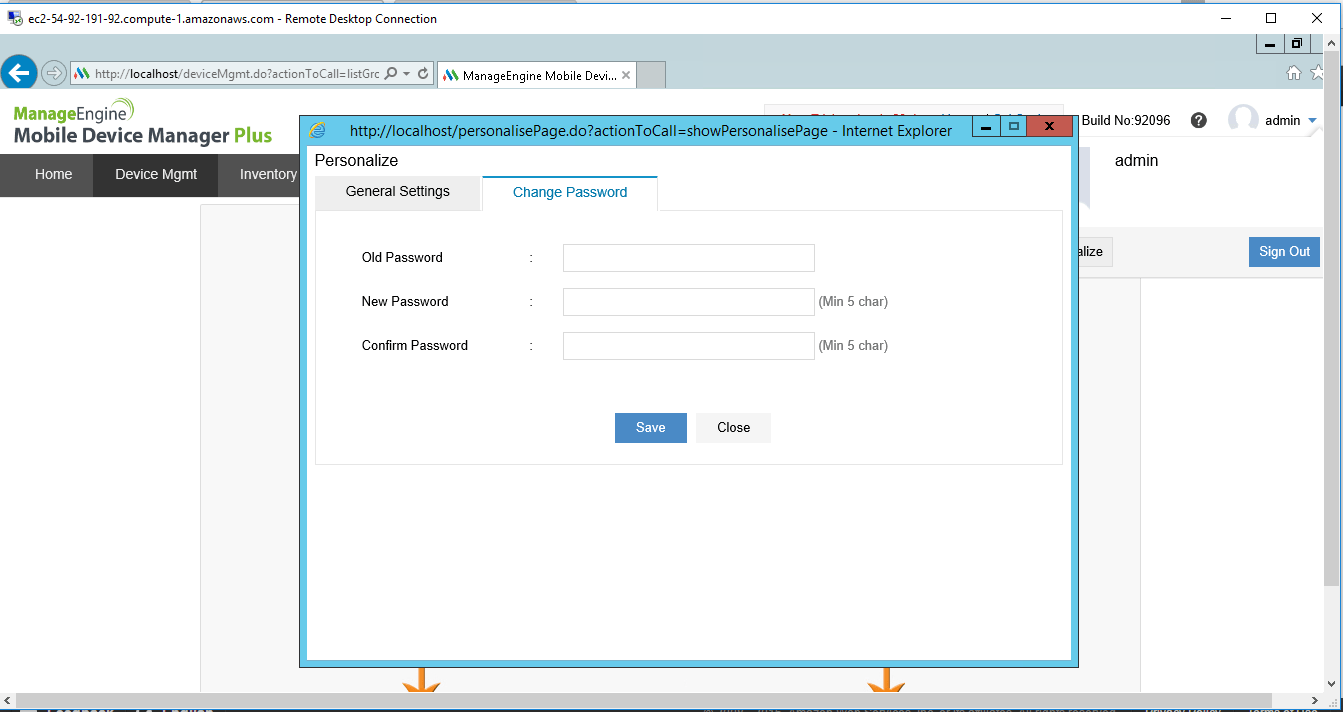
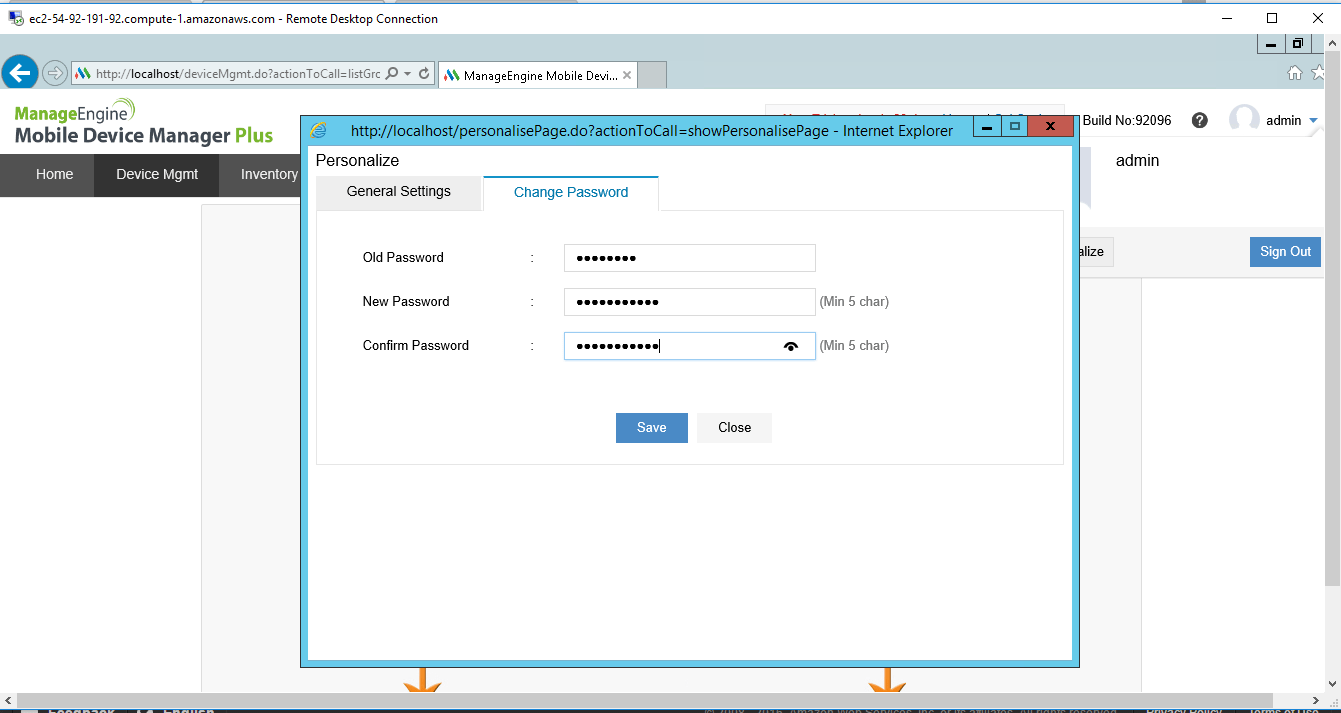
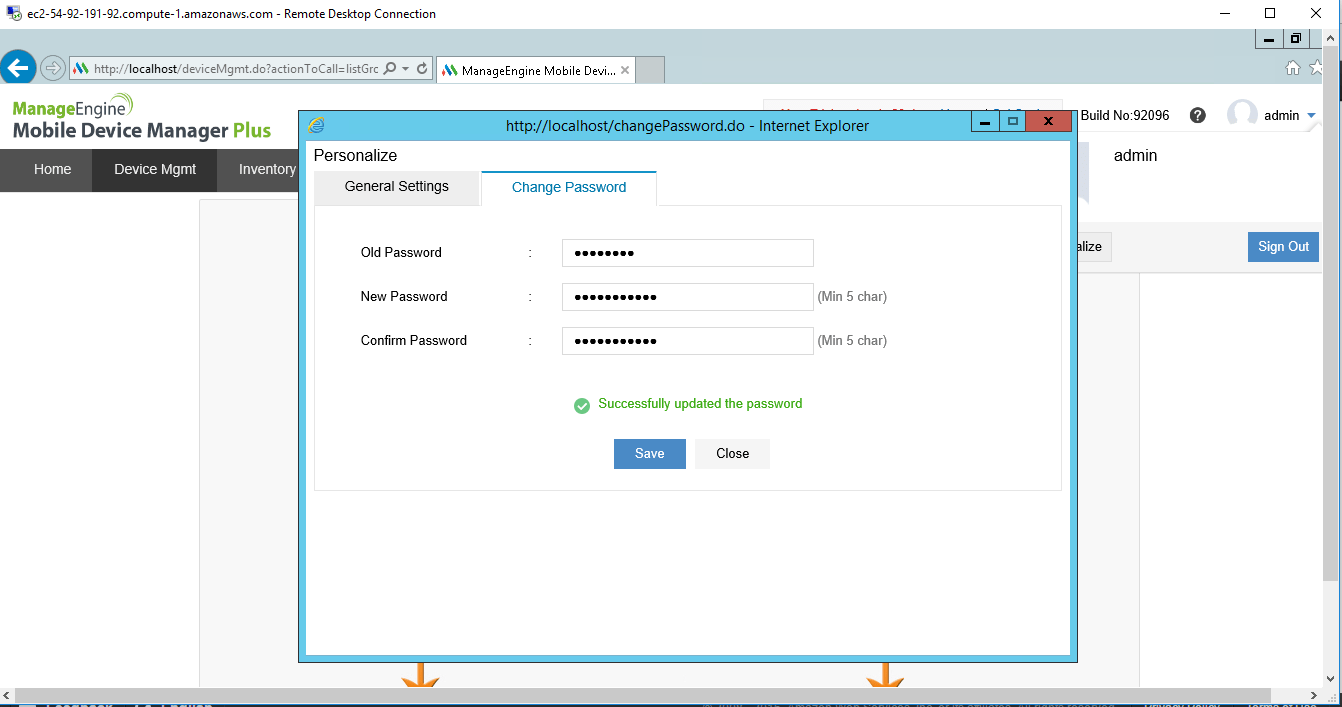
Installation Step by Step Screenshots