1-click AWS Deployment 1-click Azure Deployment 1-click Google Deployment
Overview
The purpose of Windows Server
Is asking what the purpose of Windows Server a silly question? I don’t think so. It’s a good question to ponder, especially now that the definition for servers and server workloads is changing on a regular basis. The answer to this question for Windows clients is simpler. A Windows client machine is a requester, consumer, and contributor of data.
From where is this data being pushed and pulled? What enables the mechanisms and applications running on the client operating systems to interface with this data? What secures these users and their data? The answers to these questions reveal the purpose of servers in general. They house, protect, and serve up the data to be consumed by clients.
Everything revolves around data in business today. Our email, documents, databases, customer lists—everything that we need to do business well, is data. That data is critical to us. Servers are what we use to build the fabric upon which we trust our data to reside.
We traditionally think about servers using a client-server interface mentality. A user opens a program on their client computer, this program reaches out to a server in order to retrieve something, and the server responds as needed. This idea can be correctly applied to just about every transaction you may have with a server. When your domain-joined computer needs to authenticate you as a user, it reaches out to Active Directory on the server to validate your credentials and get an authentication token. When you need to contact a resource by name, your computer asks a DNS server how to get there. If you need to open a file, you ask the file server to send it your way.
Servers are designed to be the brains of our operation, and often by doing so transparently. In recent years, large strides have been taken to ensure resources are always available and accessible in ways that don’t require training or a large effort on the part of our employees.
In most organizations, many different servers are needed in order to provide your workforce with the capabilities they require. Each service inside Windows Server is provided as, or as part of, a role. When you talk about needing new servers or configuring a new server for any particular task, what you are really referring to is the individual role or roles that are going to be configured on that server in order to get the work done. A server without any roles installed is useless, though depending on the chassis, can make an excellent paperweight. A 3U SAN device could weigh upwards of 100 pounds and keep your desk orderly even in the middle of a hurricane!
If you think of roles as the meat and potatoes of a server, then the next bit we will discuss is sort of like adding salt and pepper. Beyond the overhead roles you will install and configure on your servers, Windows also contains many features that can be installed, which sometimes stand alone, but more often complement specific roles in the operating system. Features may be something that complement and add unconventionality to the base operating system such as Telnet Client, or a feature may be added to a server in order to enhance an existing role, such as adding the Network Load Balancing feature to an already-equipped remote access or IIS server. The combination of roles and features inside Windows Server is what equips that piece of metal to do work.
This book will, quite obviously, focus on a Microsoft-centric infrastructure. In these environments, Windows Server operating system is king, and is prevalent across all facets of technology. There are alternatives to Windows Server, and different products which can provide some of the same functions to an organization, but it is quite rare to find a business environment anywhere that is running without some semblance of a Microsoft infrastructure.
Windows Server contains an incredible amount of technology, all wrapped up in one small installation disk. With Windows Server 2019, Microsoft has gotten us thinking out of the box about what it means to be a server in the first place, and comes with some exciting new capabilities that we will spend some time covering in these pages. Things such as PowerShell, Windows Admin Center, and Storage Spaces Direct are changing the way that we manage and size our computing environments; these are exciting times to be or to become a server administrator!
- We harden our images using a combination of CVE vulnerabilities from NIST, PCI, CSI, OEM’s own recommendations and industry best practices.
- In cloud computing, hardening is usually the process of securing a system by reducing its surface of vulnerability, which is larger when a system performs more functions.
- Reducing available ways of attack typically includes changing default passwords, the removal of unnecessary software, unnecessary usernames or logins, and the disabling or removal of unnecessary services.
- Hardening is what enterprises have to do to ensure all that all unnecessary default options which can lead to somebody attacking your server is closed out. So this is considered better for production deployments instead of plain vanilla deployment.
The architecture that we use allows the API to be self hosted as a windows service.
Windows Server 2019 that touched on areas such as the improvements made around hyper-converged infrastructure (HCI), hybrid capabilities such as Azure File Sync and Azure Site Recovery, our new administrative experience with the Windows Admin Center (WAC), and an array of pretty mind-blowing storage enhancements. In this article, we’ll describe some of the principles that help guide our thinking when designing security solutions and delve into a few of the innovations and enhancements we made to security in this latest Windows Server release.
Security
Security has long been a top priority in Windows Server and that continues with Windows Server 2019. Over the years, we’ve not only invested a huge amount in developing mitigation for well-known attack vectors of the day, but also in trying to better understand how the attacks evolve over time and anything they might share in common.
The table below highlights some of the more notable takeaways from our ongoing work and research.
| 1. | The network is no longer the security perimeter (it hasn’t been for some time) | Identity is the (new) security perimeter |
| 2. | Entry—we can’t stop this from happening | People will be fooled, bribed, blackmailed, etc. |
| 3. | Eliminating human error isn’t possible | Phishing works and will continue to do so |
| 4. | Insider-attacks are a big problem | Anomalous activity monitoring helps in detection; limit access through identity management and isolation |
| 5. | Compliance is very important | But compliance and security are not the same thing: compliant != secure |
| 6. | Prevention methods aren’t always technical or architectural | Many will be operational and that will impose some level of additional operational friction—security has a price $$$ |
At a high-level then, our efforts boil down to 4 core, and mostly self-explanatory guiding principles (on the left) across 3 technology dimensions (on the right). It’s worth calling out that one of those technology dimensions, managing privileged identities, has never been more important than it is today given that identity and strong authentication is steadily replacing the network as the security perimeter.

These guiding principles and areas of focus help us ensure that we not only provide reactive mitigation to what are sadly becoming commonplace threats, but that we also build in proactive measures that prevent attacks from ever starting in the first place. Stated succinctly, security isn’t a bolt-on, it’s an architectural principle and one that both Windows 10 and Windows Server 2019 are walking (well, running if you’ll excuse the pun) incarnations of. That’s enough of our mental model, let’s get on with discussing some of the new capabilities in Windows Server 2019.
The privileged identity management capabilities provided by Windows Server 2016, such as Just Enough Administration (JEA) and Credential Guard carry forward into Windows Server 2019. For the purposes of this blog then, we’ll focus on a few of the other technologies that embrace the latter two dimensions: securing the OS and providing secure fabric virtualization and virtualization-based security (VBS).
Secure the OS
Technologies for mitigating code execution attacks
This example takes us well-down into the weeds of just two of the ways that the OS protects itself by ensuring that only legitimate, whitelisted code can run and that, when it does, it runs in the manner it was intended to.
With Windows Defender Application Control (WDAC), administrators can create policies that block anything from running unless it’s included in the whitelisted policy. Because the WDAC policy is enforced by the hypervisor, its control extends even to kernel mode components like drivers.
Note that we mentioned that the policy is enforced by the hypervisor, not Hyper-V. It’s pretty easy to conflate hypervisor and Hyper-V as one and the same thing—they’re actually not the same thing. At its core, a hypervisor controls the hardware’s native virtualization capabilities and Windows uses it in two distinct ways:
- Hyper-V uses the Windows hypervisor to allow you to create and run virtual machines attached to virtual networks, etc.
- Windows itself (without Hyper-V) leverages the hypervisor’s control over the virtualization hardware extensions to isolate various OS components from one another for the purposes of OS integrity and confidentiality.
With WDAC in Windows Server 2019, you can now “stack” multiple policies on top of one another to create a whitelist that is the aggregate of all stacked policies. It’s even possible to create a policy that allows the WDAC policy to be changed without requiring a reboot!
Control Flow Guard (CFG) provides built-in platform security designed to combat intentional memory corruption vulnerabilities by placing restrictions on where an application can execute code from thereby making it much harder for malicious software to execute arbitrary code through vulnerabilities such as buffer overflows. With Windows Server 2019, we’ve added support for kernel-mode CFG, too.

Secure fabric virtualization and virtualization-based security (VBS)
Support for shielding Linux VMs
With Windows Server 2019, you’re now able to protect your Linux workloads by running them inside shielded VMs. By leveraging the same protections as Windows VMs including Secure Boot, template disk signing, a secure provisioning process, and TPM-sealed disk encryption keys, you’re able to protect data in your Linux VMs at rest and in flight when migrating the VM between two Hyper-V hosts. Under the hood, we’re leveraging the native dm-crypt disk encryption technology to enable the VM to encrypt itself and ensure the VM owner is the only entity with access to the disk encryption passphrases. Learn how to get started with Linux shielded VMs and check out the open source tools that power them.
Simplified host attestation model
In Windows Server 2019, we are introducing a new attestation mode based on asymmetric key pairs called Host Key attestation. This mode is designed to greatly simplify setup in environments where TPM attestation is not possible. It offers similar assurances to the existing Active Directory attestation mode, in that possession of the key is enough to be able to run shielded VMs, but does not require an Active Directory trust to be established (the hosts don’t even need to be domain joined). A TPM is not required on the Hyper-V host, which also means that HGS will not validate the hardware or software configuration on the host as it does with TPM mode. Check out how to deploy the Host Guardian Service and configure it and Hyper-V hosts for Host Key attestation.
Windows Admin Center
Windows Admin Center is a locally deployed, browser-based app for managing servers, clusters, hyper-converged infrastructure, and Windows 10 PCs. It comes at no additional cost beyond Windows and is ready to use in production.
You can install Windows Admin Center on Windows Server 2019 as well as Windows 10 and earlier versions of Windows and Windows Server, and use it to manage servers and clusters running Windows Server 2008 R2 and later.
Desktop experience
Because Windows Server 2019 is a Long-Term Servicing Channel (LTSC) release, it includes the Desktop Experience. (Semi-Annual Channel (SAC) releases don’t include the Desktop Experience by design; they are strictly Server Core and Nano Server container image releases.) As with Windows Server 2016, during setup of the operating system you can choose between Server Core installations or Server with Desktop Experience installations.
System Insights
System Insights is a new feature available in Windows Server 2019 that brings local predictive analytics capabilities natively to Windows Server. These predictive capabilities, each backed by a machine-learning model, locally analyze Windows Server system data, such as performance counters and events, providing insight into the functioning of your servers and helping you reduce the operational expenses associated with reactively managing issues in your Windows Server deployments.
Hybrid Cloud
Server Core app compatibility feature on demand
The Server Core App Compatibility feature on demand (FOD) significantly improves the app compatibility of the Windows Server Core installation option by including a subset of binaries and components from Windows Server with the Desktop Experience, without adding the Windows Server Desktop Experience graphical environment itself. This is done to increase the functionality and compatibility of Server Core while keeping it as lean as possible.
This optional feature on demand is available on a separate ISO and can be added to Windows Server Core installations and images only, using DISM.
Windows Defender Advanced Threat Protection (ATP)
ATP’s deep platform sensors and response actions expose memory and kernel level attacks and respond by suppressing malicious files and terminating malicious processes.
Windows Defender ATP Exploit Guard is a new set of host-intrusion prevention capabilities. The four components of Windows Defender Exploit Guard are designed to lock down the device against a wide variety of attack vectors and block behaviors commonly used in malware attacks, while enabling you to balance security risk and productivity requirements.
- Attack Surface Reduction(ASR) is set of controls that enterprises can enable to prevent malware from getting on the machine by blocking suspicious malicious files (for example, Office files), scripts, lateral movement, ransomware behavior, and email-based threats.
- Network protection protects the endpoint against web-based threats by blocking any outbound process on the device to untrusted hosts/IP addresses through Windows Defender SmartScreen.
- Controlled folder access protects sensitive data from ransomware by blocking untrusted processes from accessing your protected folders.
- Exploit protection is a set of mitigations for vulnerability exploits (replacing EMET)that can be easily configured to protect your system and applications.
Windows Defender Application Control (also known as Code Integrity (CI) policy) was released in Windows Server 2016. Customer feedback has suggested that it is a great concept, but hard to deploy. To address this, we have built default CI policies, which allows all Windows in-box files and Microsoft applications, such as SQL Server, and block known executables that can bypass CI.
Security with Software Defined Networking (SDN)
Security with SDN delivers many features to increase customer confidence in running workloads, either on-premises, or as a service provider in the cloud.
These security enhancements are integrated into the comprehensive SDN platform introduced in Windows Server 2016.
Shielded Virtual Machines improvements
- Branch office improvementsYou can now run shielded virtual machines on machines with intermittent connectivity to the Host Guardian Service by leveraging the new fallback HGS and offline mode features. Fallback HGS allows you to configure a second set of URLs for Hyper-V to try if it can’t reach your primary HGS server.Offline mode allows you to continue to start up your shielded VMs, even if HGS can’t be reached, as long as the VM has started successfully once, and the host’s security configuration has not changed.
- Troubleshooting improvementsWe’ve also made it easier to troubleshoot your shielded virtual machines by enabling support for VMConnect Enhanced Session Mode and PowerShell Direct. These tools are particularly useful if you’ve lost network connectivity to your VM and need to update its configuration to restore access.These features do not need to be configured, and they become available automatically when a shielded VM is placed on a Hyper-V host running Windows Server version 1803 or later.
- Linux supportIf you run mixed-OS environments, Windows Server 2019 now supports running Ubuntu, Red Hat Enterprise Linux, and SUSE Linux Enterprise Server inside shielded virtual machines.
HTTP/2 for a faster and safer Web
- Improved coalescing of connections to deliver an uninterrupted and properly encrypted browsing experience.
- Upgraded HTTP/2’s server-side cipher suite negotiation for automatic mitigation of connection failures and ease of deployment.
- Changed our default TCP congestion provider to Cubic to give you more throughput!
Storage
Here are some of the changes we’ve made to storage in Windows Server 2019. For details, see What’s new in Storage.
Storage Migration Service
Storage Migration Service is a new technology that makes it easier to migrate servers to a newer version of Windows Server. It provides a graphical tool that inventories data on servers, transfers the data and configuration to newer servers, and then optionally moves the identities of the old servers to the new servers so that apps and users don’t have to change anything. For more info, see Storage Migration Service.
Storage Spaces Direct
Here’s a list of what’s new in Storage Spaces Direct. For details, see What’s new in Storage Spaces Direct. Also see Azure Stack HCI for info on acquiring validated Storage Spaces Direct systems.
- Deduplication and compression for ReFS volumes
- Native support for persistent memory
- Nested resiliency for two-node hyper-converged infrastructure at the edge
- Two-server clusters using a USB flash drive as a witness
- Windows Admin Center support
- Performance history
- Scale up to 4 PB per cluster
- Mirror-accelerated parity is 2X faster
- Drive latency outlier detection
- Manually delimit the allocation of volumes to increase fault tolerance
Storage Replica
Here’s what’s new in Storage Replica. For details, see What’s new in Storage Replica.
- Storage Replica is now available in Windows Server 2019 Standard Edition.
- Test failover is a new feature that allows mounting of destination storage to validate replication or backup data. For more information, see Frequently Asked Questions about Storage Replica.
- Storage Replica log performance improvements
- Windows Admin Center support
Failover Clustering
Here’s a list of what’s new in Failover Clustering. For details, see What’s new in Failover Clustering.
- Cluster sets
- Azure-aware clusters
- Cross-domain cluster migration
- USB witness
- Cluster infrastructure improvements
- Cluster Aware Updating supports Storage Spaces Direct
- File share witness enhancements
- Cluster hardening
- Failover Cluster no longer uses NTLM authentication
Application Platform
Linux containers on Windows
It is now possible to run Windows and Linux-based containers on the same container host, using the same docker daemon. This enables you to have a heterogeneous container host environment while providing flexibility to application developers.
Built-in Support for Kubernetes
Windows Server 2019 continues the improvements to compute, networking and storage from the semi-annual channel releases needed to support Kubernetes on Windows. More details are available in upcoming Kubernetes releases.
- Container Networking in Windows Server 2019 greatly improves usability of Kubernetes on Windows by enhancing platform networking resiliency and support of container networking plugins.
- Deployed workloads on Kubernetes are able to use network security to protect both Linux and Windows services using embedded tooling.
Container improvements
- Improved integrated identityWe’ve made integrated Windows authentication in containers easier and more reliable, addressing several limitations from prior versions of Windows Server.
- Better application compatibilityContainerizing Windows-based applications just got easier: The app compatibility for the existing windowsservercore image has been increased. For applications with additional API dependencies, there is now a third base image: windows.
- Reduced size and higher performanceThe base container image download sizes, size on disk and startup times have been improved. This speeds up container workflows
- Management experience using Windows Admin Center (preview)We’ve made it easier than ever to see which containers are running on your computer and manage individual containers with a new extension for Windows Admin Center. Look for the “Containers” extension in the Windows Admin Center public feed.
Encrypted Networks
Encrypted Networks – Virtual network encryption allows encryption of virtual network traffic between virtual machines that communicate with each other within subnets marked as Encryption Enabled. It also utilizes Datagram Transport Layer Security (DTLS) on the virtual subnet to encrypt packets. DTLS protects against eavesdropping, tampering, and forgery by anyone with access to the physical network.
Network performance improvements for virtual workloads
Network performance improvements for virtual workloads maximizes the network throughput to virtual machines without requiring you to constantly tune or over-provision your host. This lowers the operations and maintenance cost while increasing the available density of your hosts. These new features are:
- Receive Segment Coalescing in the vSwitch
- Dynamic Virtual Machine Multi-Queue (d.VMMQ)
Low Extra Delay Background Transport
Low Extra Delay Background Transport (LEDBAT) is a latency optimized, network congestion control provider designed to automatically yield bandwidth to users and applications, while consuming the entire bandwidth available when the network is not in use.
This technology is intended for use in deploying large, critical updates across an IT environment without impacting customer facing services and associated bandwidth.
Windows Time Service
The Windows Time Service includes true UTC-compliant leap second support, a new time protocol called Precision Time Protocol, and end-to-end traceability.
High performance SDN gateways
High performance SDN gateways in Windows Server 2019 greatly improves the performance for IPsec and GRE connections, providing ultra-high-performance throughput with much less CPU utilization.
New Deployment UI and Windows Admin Center extension for SDN
Now, with Windows Server 2019, it’s easy to deploy and manage through a new deployment UI and Windows Admin Center extension that enable anyone to harness the power of SDN.
Persistent Memory support for Hyper-V VMs
To leverage the high throughput and low latency of persistent memory (a.k.a. storage class memory) in virtual machines, it can now be projected directly into VMs. This can help to drastically reduce database transaction latency or reduce recovery times for low latency in-memory databases on failure.
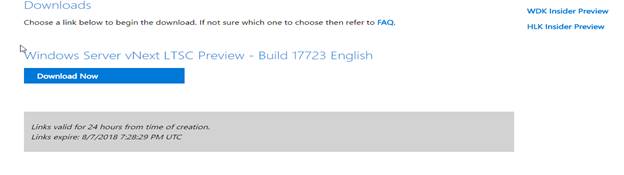
Step By Step Installation Of Windows Server 2019 Standard
- Processor – 1.4 GHz 64-bit processor
- RAM – 512 MB
- Disk Space – 32 GB
- Network – Gigabit (10/100/1000baseT) Ethernet adapter
- Optical Storage – DVD drive (if installing the OS from DVD media)
- Video – Super VGA (1024 x 768) or higher-resolution (optional)
- Input Devices – Keyboard and mouse (optional)
- Internet – Broadband access (optional)

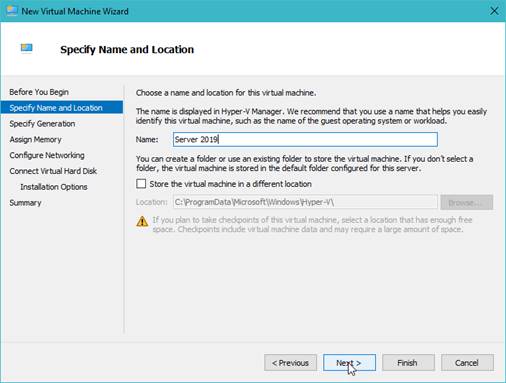
Naming the Hyper-V so it is easy to identify
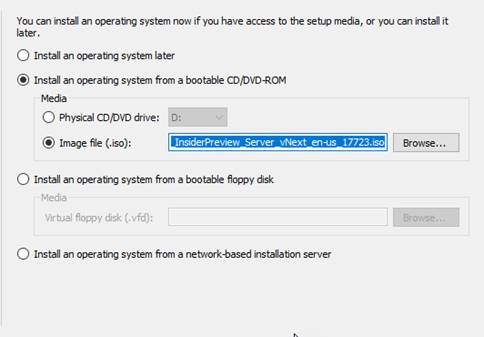
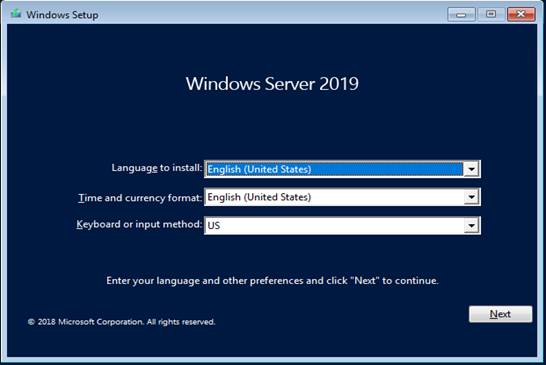
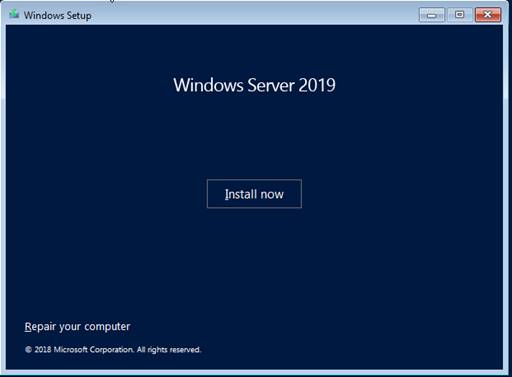
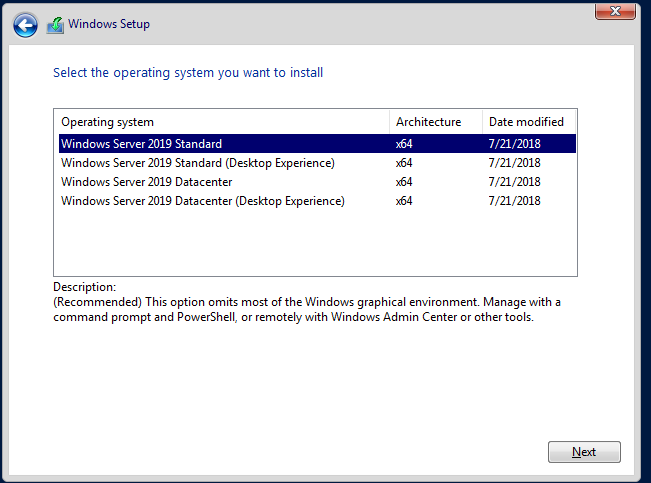
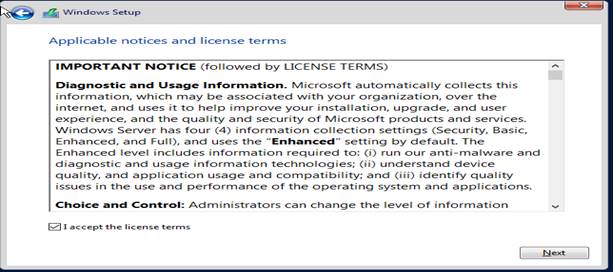
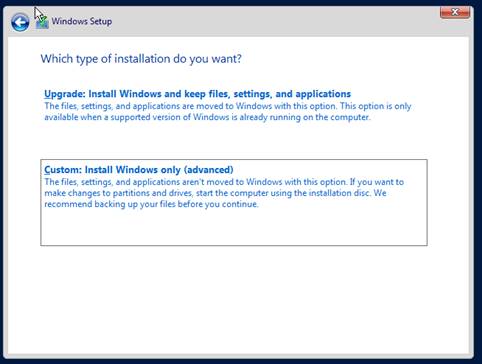
Custom – Fresh install
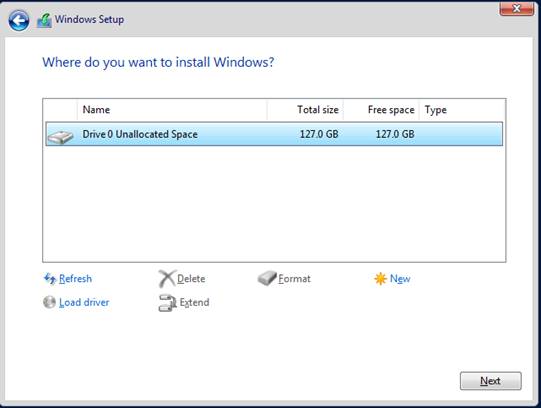
HDD as per default,
Features
Major Features of Hardened Windows Server 2019
-
1. Hybrid Cloud & Azure
Nowadays it is impossible to imagine an IT landscape without virtualization and hybrid clouds. Hence in this version of Windows, Microsoft improves the connections between its Azure cloud platform and Windows Server operating system. The connection is not limited to the Admin Center, the Azure Network Adapter also connects to the cloud computing platform of the local server. Furthermore, this version also includes better support for Azure Backup, File Sync, disaster recovery, and all other Azure services.
2. Linux Support
What sets this new version apart is that you can run mixed OS-environments. Windows Server 2019 has made it easier to integrate Linux. It supports running Ubuntu, Red Hat Enterprise Linux, and SUSE Linux Enterprise Server inside shielded virtual machines. Moreover, Linux distributions can be easily downloaded from the Microsoft Store.
3. Security
Windows Server 2019 has also new security measures. A new set of host intrusion prevention capabilities known as, Windows Defender Advanced Threat Protection (ATP) has been implemented in this version. This precautionary protection measurement monitors the server from malware and stops processes that are possibly dangerous. Furthermore, it also includes attack detection and zero-day exploits. Another security feature that we would like to highlight is HGS offline mode for shielded VMs. This feature allows you to turn on your virtual machines even when HGS can’t be reached.
4. Storage
The new version also includes changes in the storage area. It includes a completely new feature called Storage Migration Service. This new feature helps you to migrate your servers to a newer version of Windows Server. It also ensures an easier migration to the cloud. In addition to this, Storage Space direct has also been improved. In this feature, you can expect more stability and higher speed from the server.
Azure
Note: How to find PublicDNS in Azure
Step1 ) RDP Connection: To connect to the deployed instance, Please follow Instructions to Connect to Windows instance on Azure Cloud
Connect to virtual machine using following RDP credentials:
- Hostname: PublicDNS / IP of machine
- Port : 3389
Username: Your chosen username when you created the machine ( For example: Azureuser)
Password : Your Chosen Password when you created the machine ( How to reset the password if you do not remember)
Step 2) Other Information:
1.Default ports:
- Windows Machines: RDP Port – 3389
- Http: 80
- Https: 443
Configure custom inbound and outbound rules using this link
AWS
Installation Instructions for Windows
Note: How to find PublicDNS in AWS
Step 1) RDP Connection: To connect to the deployed instance, Please follow Instructions to Connect to Windows instance on AWS Cloud
1) Connect to the virtual machine using following RDP credentials:
- Hostname: PublicDNS / IP of machine
- Port : 3389
Username: To connect to the operating system, use RDP and the username is Administrator.
Password: Please Click here to know how to get password .
Step 2) Other Information:
Default ports:
- Windows Machines: RDP Port – 3389
- Http: 80
- Https: 443
Configure custom inbound and outbound rules using this link
GCP
Installation Instructions For Windows
Step 1) VM Creation:
i) Click the Launch on Compute Engine button to choose the hardware and network settings.
ii) You can see at this page, an overview of Cognosys Image as well as some estimated costs of VM.
ii) In the settings page, you can choose the number of CPUs and amount of RAM, the disk size and type etc.
Step 2) RDP Connection: To initialize the DB Server connect to the deployed instance, Please follow Instructions to Connect to Windows instance on Google Cloud
Step 3) Other Information:
Default ports:
- Windows Machines: RDP Port – 3389
- Http: 80
- Https: 443


